关于一种以“bill”开头的变异MD5加密方式的破解方法,Asp 变异 MD5 加密模块。
偶然间看到个求解密帖子,大概研究了下,做一下记录,以后可能用得着。
原帖标题为:求教一个md5加密算法怎么解密!
内容为:
<%
Private Const BITS_TO_A_BYTE = 8
Private Const BYTES_TO_A_WORD = 4
Private Const BITS_TO_A_WORD = 32
Private m_lOnBits(30)
Private m_l2Power(30)
Private Function LShift(lValue, iShiftBits)
If iShiftBits = 0 Then
LShift = lValue
Exit Function
ElseIf iShiftBits = 31 Then
If lValue And 1 Then
LShift = &H80000000
Else
LShift = 0
End If
Exit Function
ElseIf iShiftBits < 0 Or iShiftBits > 31 Then
Err.Raise 6
End If
If (lValue And m_l2Power(31 - iShiftBits)) Then
LShift = ((lValue And m_lOnBits(31 - (iShiftBits + 1))) * m_l2Power(iShiftBits)) Or &H80000000
Else
LShift = ((lValue And m_lOnBits(31 - iShiftBits)) * m_l2Power(iShiftBits))
End If
End Function
Private Function RShift(lValue, iShiftBits)
If iShiftBits = 0 Then
RShift = lValue
Exit Function
ElseIf iShiftBits = 31 Then
If lValue And &H80000000 Then
RShift = 1
Else
RShift = 0
End If
Exit Function
ElseIf iShiftBits < 0 Or iShiftBits > 31 Then
Err.Raise 6
End If
RShift = (lValue And &H7FFFFFFE) \ m_l2Power(iShiftBits)
If (lValue And &H80000000) Then
RShift = (RShift Or (&H40000000 \ m_l2Power(iShiftBits - 1)))
End If
End Function
Private Function RotateLeft(lValue, iShiftBits)
RotateLeft = LShift(lValue, iShiftBits) Or RShift(lValue, (32 - iShiftBits))
End Function
Private Function AddUnsigned(lX, lY)
Dim lX4
Dim lY4
Dim lX8
Dim lY8
Dim lResult
lX8 = lX And &H80000000
lY8 = lY And &H80000000
lX4 = lX And &H40000000
lY4 = lY And &H40000000
lResult = (lX And &H3FFFFFFF) + (lY And &H3FFFFFFF)
If lX4 And lY4 Then
lResult = lResult Xor &H80000000 Xor lX8 Xor lY8
ElseIf lX4 Or lY4 Then
If lResult And &H40000000 Then
lResult = lResult Xor &HC0000000 Xor lX8 Xor lY8
Else
lResult = lResult Xor &H40000000 Xor lX8 Xor lY8
End If
Else
lResult = lResult Xor lX8 Xor lY8
End If
AddUnsigned = lResult
End Function
Private Function md5_F(x, y, z)
md5_F = (x And y) Or ((Not x) And z)
End Function
Private Function md5_G(x, y, z)
md5_G = (x And z) Or (y And (Not z))
End Function
Private Function md5_H(x, y, z)
md5_H = (x Xor y Xor z)
End Function
Private Function md5_I(x, y, z)
md5_I = (y Xor (x Or (Not z)))
End Function
Private Sub md5_FF(a, b, c, d, x, s, ac)
a = AddUnsigned(a, AddUnsigned(AddUnsigned(md5_F(b, c, d), x), ac))
a = RotateLeft(a, s)
a = AddUnsigned(a, b)
End Sub
Private Sub md5_GG(a, b, c, d, x, s, ac)
a = AddUnsigned(a, AddUnsigned(AddUnsigned(md5_G(b, c, d), x), ac))
a = RotateLeft(a, s)
a = AddUnsigned(a, b)
End Sub
Private Sub md5_HH(a, b, c, d, x, s, ac)
a = AddUnsigned(a, AddUnsigned(AddUnsigned(md5_H(b, c, d), x), ac))
a = RotateLeft(a, s)
a = AddUnsigned(a, b)
End Sub
Private Sub md5_II(a, b, c, d, x, s, ac)
a = AddUnsigned(a, AddUnsigned(AddUnsigned(md5_I(b, c, d), x), ac))
a = RotateLeft(a, s)
a = AddUnsigned(a, b)
End Sub
Private Function ConvertToWordArray(sMessage)
Dim lMessageLength
Dim lNumberOfWords
Dim lWordArray()
Dim lBytePosition
Dim lByteCount
Dim lWordCount
Const MODULUS_BITS = 512
Const CONGRUENT_BITS = 448
lMessageLength = Len(sMessage)
lNumberOfWords = (((lMessageLength + ((MODULUS_BITS - CONGRUENT_BITS) \ BITS_TO_A_BYTE)) \ (MODULUS_BITS \ BITS_TO_A_BYTE)) + 1) * (MODULUS_BITS \ BITS_TO_A_WORD)
ReDim lWordArray(lNumberOfWords - 1)
lBytePosition = 0
lByteCount = 0
Do Until lByteCount >= lMessageLength
lWordCount = lByteCount \ BYTES_TO_A_WORD
lBytePosition = (lByteCount Mod BYTES_TO_A_WORD) * BITS_TO_A_BYTE
lWordArray(lWordCount) = lWordArray(lWordCount) Or LShift(Asc(Mid(sMessage, lByteCount + 1, 1)), lBytePosition)
lByteCount = lByteCount + 1
Loop
lWordCount = lByteCount \ BYTES_TO_A_WORD
lBytePosition = (lByteCount Mod BYTES_TO_A_WORD) * BITS_TO_A_BYTE
lWordArray(lWordCount) = lWordArray(lWordCount) Or LShift(&H80, lBytePosition)
lWordArray(lNumberOfWords - 2) = LShift(lMessageLength, 3)
lWordArray(lNumberOfWords - 1) = RShift(lMessageLength, 29)
ConvertToWordArray = lWordArray
End Function
Private Function WordToHex(lValue)
Dim lByte
Dim lCount
For lCount = 0 To 3
lByte = RShift(lValue, lCount * BITS_TO_A_BYTE) And m_lOnBits(BITS_TO_A_BYTE - 1)
WordToHex = WordToHex & Right("0" & Hex(lByte), 2)
Next
End Function
Public Function MD5(sMessage)
m_lOnBits(0) = CLng(1)
m_lOnBits(1) = CLng(3)
m_lOnBits(2) = CLng(7)
m_lOnBits(3) = CLng(15)
m_lOnBits(4) = CLng(31)
m_lOnBits(5) = CLng(63)
m_lOnBits(6) = CLng(127)
m_lOnBits(7) = CLng(255)
m_lOnBits(8) = CLng(511)
m_lOnBits(9) = CLng(1023)
m_lOnBits(10) = CLng(2047)
m_lOnBits(11) = CLng(4095)
m_lOnBits(12) = CLng(8191)
m_lOnBits(13) = CLng(16383)
m_lOnBits(14) = CLng(32767)
m_lOnBits(15) = CLng(65535)
m_lOnBits(16) = CLng(131071)
m_lOnBits(17) = CLng(262143)
m_lOnBits(18) = CLng(524287)
m_lOnBits(19) = CLng(1048575)
m_lOnBits(20) = CLng(2097151)
m_lOnBits(21) = CLng(4194303)
m_lOnBits(22) = CLng(8388607)
m_lOnBits(23) = CLng(16777215)
m_lOnBits(24) = CLng(33554431)
m_lOnBits(25) = CLng(67108863)
m_lOnBits(26) = CLng(134217727)
m_lOnBits(27) = CLng(268435455)
m_lOnBits(28) = CLng(536870911)
m_lOnBits(29) = CLng(1073741823)
m_lOnBits(30) = CLng(2147483647)
m_l2Power(0) = CLng(1)
m_l2Power(1) = CLng(2)
m_l2Power(2) = CLng(4)
m_l2Power(3) = CLng(8)
m_l2Power(4) = CLng(16)
m_l2Power(5) = CLng(32)
m_l2Power(6) = CLng(64)
m_l2Power(7) = CLng(128)
m_l2Power(8) = CLng(256)
m_l2Power(9) = CLng(512)
m_l2Power(10) = CLng(1024)
m_l2Power(11) = CLng(2048)
m_l2Power(12) = CLng(4096)
m_l2Power(13) = CLng(8192)
m_l2Power(14) = CLng(16384)
m_l2Power(15) = CLng(32768)
m_l2Power(16) = CLng(65536)
m_l2Power(17) = CLng(131072)
m_l2Power(18) = CLng(262144)
m_l2Power(19) = CLng(524288)
m_l2Power(20) = CLng(1048576)
m_l2Power(21) = CLng(2097152)
m_l2Power(22) = CLng(4194304)
m_l2Power(23) = CLng(8388608)
m_l2Power(24) = CLng(16777216)
m_l2Power(25) = CLng(33554432)
m_l2Power(26) = CLng(67108864)
m_l2Power(27) = CLng(134217728)
m_l2Power(28) = CLng(268435456)
m_l2Power(29) = CLng(536870912)
m_l2Power(30) = CLng(1073741824)
Dim x
Dim k
Dim AA
Dim BB
Dim CC
Dim DD
Dim a
Dim b
Dim c
Dim d
Const S11 = 7
Const S12 = 12
Const S13 = 17
Const S14 = 22
Const S21 = 5
Const S22 = 9
Const S23 = 14
Const S24 = 20
Const S31 = 4
Const S32 = 11
Const S33 = 16
Const S34 = 23
Const S41 = 6
Const S42 = 10
Const S43 = 15
Const S44 = 21
x = ConvertToWordArray(sMessage)
a = &H67452301
b = &HEFCDAB89
c = &H98BADCFE
d = &H10325476
For k = 0 To UBound(x) Step 16
AA = a
BB = b
CC = c
DD = d
md5_FF a, b, c, d, x(k + 0), S11, &HD76AA478
md5_FF d, a, b, c, x(k + 1), S12, &HE8C7B756
md5_FF c, d, a, b, x(k + 2), S13, &H242070DB
md5_FF b, c, d, a, x(k + 3), S14, &HC1BDCEEE
md5_FF a, b, c, d, x(k + 4), S11, &HF57C0FAF
md5_FF d, a, b, c, x(k + 5), S12, &H4787C62A
md5_FF c, d, a, b, x(k + 6), S13, &HA8304613
md5_FF b, c, d, a, x(k + 7), S14, &HFD469501
md5_FF a, b, c, d, x(k + 8), S11, &H698098D8
md5_FF d, a, b, c, x(k + 9), S12, &H8B44F7AF
md5_FF c, d, a, b, x(k + 10), S13, &HFFFF5BB1
md5_FF b, c, d, a, x(k + 11), S14, &H895CD7BE
md5_FF a, b, c, d, x(k + 12), S11, &H6B901122
md5_FF d, a, b, c, x(k + 13), S12, &HFD987193
md5_FF c, d, a, b, x(k + 14), S13, &HA679438E
md5_FF b, c, d, a, x(k + 15), S14, &H49B40821
md5_GG a, b, c, d, x(k + 1), S21, &HF61E2562
md5_GG d, a, b, c, x(k + 6), S22, &HC040B340
md5_GG c, d, a, b, x(k + 11), S23, &H265E5A51
md5_GG b, c, d, a, x(k + 0), S24, &HE9B6C7AA
md5_GG a, b, c, d, x(k + 5), S21, &HD62F105D
md5_GG d, a, b, c, x(k + 10), S22, &H2441453
md5_GG c, d, a, b, x(k + 15), S23, &HD8A1E681
md5_GG b, c, d, a, x(k + 4), S24, &HE7D3FBC8
md5_GG a, b, c, d, x(k + 9), S21, &H21E1CDE6
md5_GG d, a, b, c, x(k + 14), S22, &HC33707D6
md5_GG c, d, a, b, x(k + 3), S23, &HF4D50D87
md5_GG b, c, d, a, x(k + 8), S24, &H455A14ED
md5_GG a, b, c, d, x(k + 13), S21, &HA9E3E905
md5_GG d, a, b, c, x(k + 2), S22, &HFCEFA3F8
md5_GG c, d, a, b, x(k + 7), S23, &H676F02D9
md5_GG b, c, d, a, x(k + 12), S24, &H8D2A4C8A
md5_HH a, b, c, d, x(k + 5), S31, &HFFFA3942
md5_HH d, a, b, c, x(k + 8), S32, &H8771F681
md5_HH c, d, a, b, x(k + 11), S33, &H6D9D6122
md5_HH b, c, d, a, x(k + 14), S34, &HFDE5380C
md5_HH a, b, c, d, x(k + 1), S31, &HA4BEEA44
md5_HH d, a, b, c, x(k + 4), S32, &H4BDECFA9
md5_HH c, d, a, b, x(k + 7), S33, &HF6BB4B60
md5_HH b, c, d, a, x(k + 10), S34, &HBEBFBC70
md5_HH a, b, c, d, x(k + 13), S31, &H289B7EC6
md5_HH d, a, b, c, x(k + 0), S32, &HEAA127FA
md5_HH c, d, a, b, x(k + 3), S33, &HD4EF3085
md5_HH b, c, d, a, x(k + 6), S34, &H4881D05
md5_HH a, b, c, d, x(k + 9), S31, &HD9D4D039
md5_HH d, a, b, c, x(k + 12), S32, &HE6DB99E5
md5_HH c, d, a, b, x(k + 15), S33, &H1FA27CF8
md5_HH b, c, d, a, x(k + 2), S34, &HC4AC5665
md5_II a, b, c, d, x(k + 0), S41, &HF4292244
md5_II d, a, b, c, x(k + 7), S42, &H432AFF97
md5_II c, d, a, b, x(k + 14), S43, &HAB9423A7
md5_II b, c, d, a, x(k + 5), S44, &HFC93A039
md5_II a, b, c, d, x(k + 12), S41, &H655B59C3
md5_II d, a, b, c, x(k + 3), S42, &H8F0CCC92
md5_II c, d, a, b, x(k + 10), S43, &HFFEFF47D
md5_II b, c, d, a, x(k + 1), S44, &H85845DD1
md5_II a, b, c, d, x(k + 8), S41, &H6FA87E4F
md5_II d, a, b, c, x(k + 15), S42, &HFE2CE6E0
md5_II c, d, a, b, x(k + 6), S43, &HA3014314
md5_II b, c, d, a, x(k + 13), S44, &H4E0811A1
md5_II a, b, c, d, x(k + 4), S41, &HF7537E82
md5_II d, a, b, c, x(k + 11), S42, &HBD3AF235
md5_II c, d, a, b, x(k + 2), S43, &H2AD7D2BB
md5_II b, c, d, a, x(k + 9), S44, &HEB86D391
a = AddUnsigned(a, AA)
b = AddUnsigned(b, BB)
c = AddUnsigned(c, CC)
d = AddUnsigned(d, DD)
Next
Dim MD0, MD1, MD2, MD3, MD4
MD0 = MD0 & Left(WordToHex(b), 2)
MD0 = MD0 & Right(WordToHex(d), 2)
MD1 = MD1 & Left(WordToHex(a), 1)
MD1 = MD1 & Left(WordToHex(b), 1)
MD1 = MD1 & Left(WordToHex(c), 1)
MD1 = MD1 & Right(WordToHex(a), 1)
MD1 = MD1 & Right(WordToHex(b), 1)
MD1 = MD1 & Left(WordToHex(a), 1)
MD2 = MD2 & Right(Asc(Mid(WordToHex(c), 5, 1)), 1)
MD2 = MD2 & Left(Asc(Mid(WordToHex(d), 2, 1)), 1)
MD2 = MD2 & Left(Asc(Mid(WordToHex(c), 6, 1)), 1)
MD2 = MD2 & Right(Asc(Mid(WordToHex(d), 6, 1)), 1)
MD2 = MD2 & Right(Mid(WordToHex(d), 6, 1), 1)
MD2 = MD2 & Left(Mid(WordToHex(b), 6, 1), 1)
MD3 = MD3 & Left(WordToHex(c), 6)
MD4 = MD4 & Mid(WordToHex(a), 4, 3)
MD4 = MD4 & Right(WordToHex(b), 3)
MD5 = "bill" & MD0 & MD2 & MD1 & MD4 & MD3
MD5 = LCase(MD5)
End Function
%>
加密之后是类似 bill5b876549e4b5cfcbac248cc405b1 这种密码。
Dim MD0, MD1, MD2, MD3, MD4 MD0 = MD0 & Left(WordToHex(b), 2) MD0 = MD0 & Right(WordToHex(d), 2) MD1 = MD1 & Left(WordToHex(a), 1) MD1 = MD1 & Left(WordToHex(b), 1) MD1 = MD1 & Left(WordToHex(c), 1) MD1 = MD1 & Right(WordToHex(a), 1) MD1 = MD1 & Right(WordToHex(b), 1) MD1 = MD1 & Left(WordToHex(a), 1) MD2 = MD2 & Right(Asc(Mid(WordToHex(c), 5, 1)), 1) MD2 = MD2 & Left(Asc(Mid(WordToHex(d), 2, 1)), 1) MD2 = MD2 & Left(Asc(Mid(WordToHex(c), 6, 1)), 1) MD2 = MD2 & Right(Asc(Mid(WordToHex(d), 6, 1)), 1) MD2 = MD2 & Right(Mid(WordToHex(d), 6, 1), 1) MD2 = MD2 & Left(Mid(WordToHex(b), 6, 1), 1) MD3 = MD3 & Left(WordToHex(c), 6) MD4 = MD4 & Mid(WordToHex(a), 4, 3) MD4 = MD4 & Right(WordToHex(b), 3) MD5 = "bill" & MD0 & MD2 & MD1 & MD4 & MD3 MD5 = LCase(MD5)
除了最底下这段,上边的是标准的MD5加密模块。
一个自定义的拼接字符串的算法,等会,我看看能不能逆出来标准的MD5。
Dim MD0, MD1, MD2, MD3, MD4 MD0 = MD0 & Left(WordToHex(b), 2) MD0 = MD0 & Right(WordToHex(d), 2) MD1 = MD1 & Left(WordToHex(a), 1) MD1 = MD1 & Left(WordToHex(b), 1) MD1 = MD1 & Left(WordToHex(c), 1) MD1 = MD1 & Right(WordToHex(a), 1) MD1 = MD1 & Right(WordToHex(b), 1) MD1 = MD1 & Left(WordToHex(a), 1) MD2 = MD2 & Right(Asc(Mid(WordToHex(c), 5, 1)), 1) MD2 = MD2 & Left(Asc(Mid(WordToHex(d), 2, 1)), 1) MD2 = MD2 & Left(Asc(Mid(WordToHex(c), 6, 1)), 1) MD2 = MD2 & Right(Asc(Mid(WordToHex(d), 6, 1)), 1) MD2 = MD2 & Right(Mid(WordToHex(d), 6, 1), 1) MD2 = MD2 & Left(Mid(WordToHex(b), 6, 1), 1) MD3 = MD3 & Left(WordToHex(c), 6) MD4 = MD4 & Mid(WordToHex(a), 4, 3) MD4 = MD4 & Right(WordToHex(b), 3) MD5 = "bill" & MD0 & MD2 & MD1 & MD4 & MD3 MD5 = LCase(MD5) ------------------------------------------------ Hash = bill5b876549e4b5cfcbac248cc405b1 Hash = bill 5b87 6549e4 b5cfcb ac248c c405b1 MD0 = 5b87 MD1 = b5cfcb MD2 = 6549e4 MD3 = c405b1 MD4 = ac248c a = b??ac2?f b = 5b???48c c = c405b1?? d = ??????87 '可以还原出abcd的值,由于太过于蛋疼,这里我只还原一部分,作为演示。 MD5 16 = bc MD5 32 = abcd
明文密码:123456
标准密文:e10adc3949ba59abbe56e057f20f883e
变异密文:bill493e954689e4b9beadc9abbe56e0
还原变异:e??adc?949???9abbe56e0???*???83e
字符说明:? = 任意字母或数字,* = 一定范围内的字母或数字。
在密文变异的处理中,丢失了很多值,还有很多非固定值,如上所示。
理论上可以碰撞Hash,因为丢失的值可以为任意数。
也就是说这个加密后的结果,对应多个标准MD5值,也就是对应多个明文密码。
楼主可以给出一个加密后得值,可以找出多个可能的MD5值,目测大概最少有 (6+10)^12=281474976710656 个,还不算那些非固定的,当然,能以字符方式显示的明文密码要少很多,因为很多字符为不可显示字符,然后破解其中任意一条即可通过密码认证。
由于丢失了部分值,所以原加密字符串不得而知,但是可以肯定,原加密字符串就在这些碰撞出来的MD5之中。
总之,你只要拿到加密后得值,就可以还原出多条标准MD5密文,由于是可碰撞的,所以破解几率极高。
另外说一下,这他妈的就是一傻逼变异方式,由于可碰撞的密码数量极多!极容易通过碰撞算法解出密码,通过密码校验。。。。
已写出解密算法:
Private Function RndChr(R As String) As String
Dim I As Long
Randomize
For I = 1 To Len(R)
If Mid(R, I, 1) = " " Then
If Int((2 * Rnd) + 1) = 1 Then
R = Left(R, I - 1) & Chr(Int((57 - 48 + 1) * Rnd + 48)) & Mid(R, I + 1) '随机数字
Else
R = Left(R, I - 1) & Chr(Int((102 - 97 + 1) * Rnd + 97)) & Mid(R, I + 1) '随机字母
End If
End If
Next
RndChr = R
End Function
Private Function DeCode(s As String) As String
Dim I As Long, II As Long, M(28) As String, x As String, a As String, b As String, c As String, d As String
'---------------------------------------------------------------------------
M(0) = " "
For I = 1 To 28
M(I) = Mid(s, I + 4, 1)
Next
'---------------------------------------------------------------------------
a = M(16) & M(0) & M(0) & M(17) & M(18) & M(19) & M(0) & M(14)
b = M(1) & M(2) & M(0) & M(0) & M(0) & M(20) & M(21) & M(22)
c = M(23) & M(24) & M(25) & M(26) & M(27) & M(28) & M(0) & M(0)
'---------------------------------------------------------------------------
'针对【MD2 = MD2 & Left(Asc(Mid(WordToHex(d), 2, 1)), 1)】的碰撞循环
If Val(M(6)) < 6 Then
I = IIf(Val(M(6)) > 4, 50, 48) '数字(48-57)
Else
I = IIf(Val(M(6)) > 6, 70, 65) '大写字母(65-70)
End If
Do While ((I < IIf(Val(M(6)) < 6, 58, 71)) And I <= Val(M(6) & "9"))
d = M(0) & Chr(I) & M(0) & M(0) & M(0) & M(9) & M(3) & M(4)
'x = x & LCase(a & b & c & d) & vbCrLf
For II = 1 To 100 '循环100次,取100个随机MD5值
x = x & RndChr(LCase(a & b & c & d)) & vbCrLf
Next
I = I + 1
Loop
'---------------------------------------------------------------------------
DeCode = x
End Function
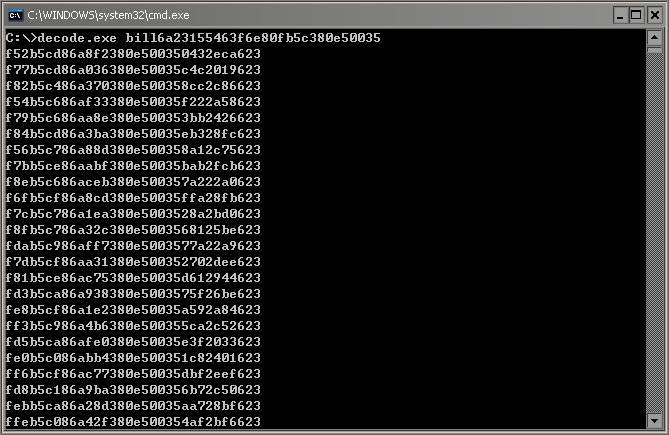
每次生成100个随机碰撞出来的标准MD5值,然后拿去批量破解吧,随意破解一个即可。
同时给出编译好的程序下载地址:http://115.com/file/cl05p21e
用法:decode.exe billd6d79457c8cdd6ac9a681ad36014
留言评论(旧系统):