I can confirm, the zero-day season is really not over yet. Less than three weeks after the discovery of the Java SE 7 0day, aka CVE-2012-4681, potentially used by the Nitro gang in targeted attacks, a potential Microsoft Internet Explorer 7 and 8 zero-day is actually exploited in the wild.
First I would like to thanks the nice people (@binjo, @_sinn3r and all the guys of the Metasploit IRC channel on freenode) how helped me to understand and go further in my investigations.
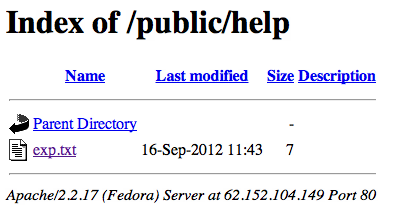
Since the release of the Java SE 7 0day I was monitoring some of the infected servers used by the alleged Nitro gang. The 14th September morning, I discovered a “/public/help” folder on one of these servers, the Italian one (smile to @PhysicalDrive0).
As seen in the following screenshot, 4 files were hosted in this folder, and as a curious man, I downloaded everything to see what was related to these files.
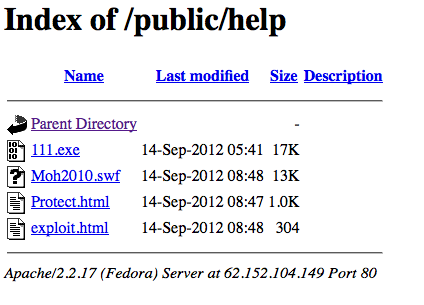
I tested these files on an up-to-date Microsoft Windows XP Pro SP3 with an up-to-date Adobe Flash (11,4,402,265). Surprise they dropped files on my test computer (See demonstration video here under) ! A new 0day ? I decide then to take a deeper look at the grabbed files.
video: http://www.youtube.com/embed/_w8XCwdw5FI
exploit.html
This file is recognized as an HTML file, and catched by 0 anti-viruses on VirusTotal (9d66323794d493a1deaab66e36d36a820d814ee4dd50d64cddf039c2a06463a5).
“exploit.html” is the entry point of the attack. This file creates an array of “img” and load “Moh2010.swf” Flash file.
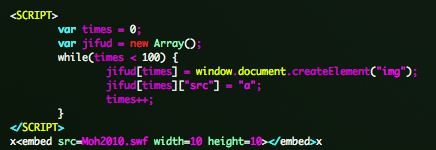
Moh2010.swf
This file is recognized as a Macromedia Flash Player movie, and catched by 0 anti-viruses on VirusTotal (70f6a2c2976248221c251d9965ff2313bc0ed0aebb098513d76de6d8396a7125).

You can observe that the file is packed by DoSWF and that it is decompress in the memory. After decompression “Moh2010.swf” file is spraying the heap and eval an iframe to ”Protect.html” file.
The ActionScript embedded in the original packed SWF file, is also interesting, you will see some special encoding (Chinese ?).
Decoded SWF file, is known as “Exploit:SWF/CVE-2010-2884.B”, or “SWF:Dropper” on VirusTotal (dd41efa629c7f7f876362c5ca6d570be6b83728a2ce8ecbef65bdb89cb402b0f) and detected only by 3/34 anti-viruses. Thanks to binjo.
This file, during exploitation is also checking if the web site is present in Flash Website Storage Settings pannel to no more load the “Protect.html” file. This mean, that once infected the user will no more be exploited despite further visites to the web site.
Display on the first visit
![]()
Display on successful exploitation
![]()
Display on further visits
![]()
Protect.html
This file is recognized as a HTML file, and catched by 0 anti-viruses on VirusTotal (2a2e2efffa382663ba10c492f407dda8a686a777858692d073712d1cc9c5f265).
If you take a look at the source code, you can see interesting javascript code, how is manipulating the “img“ array created by “exploit.html“.
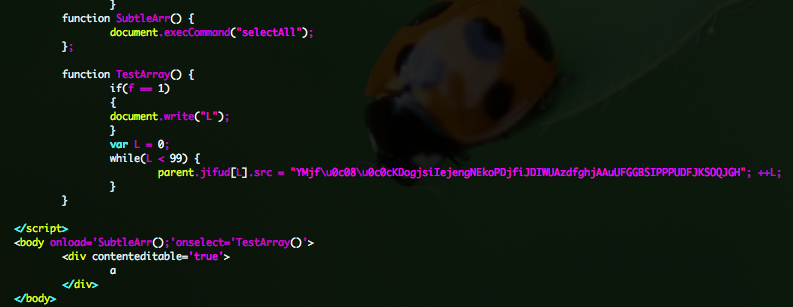
You will also see that tests are done, in order to target Windows XP 32-bit and Internet Explorer 7 or 8.
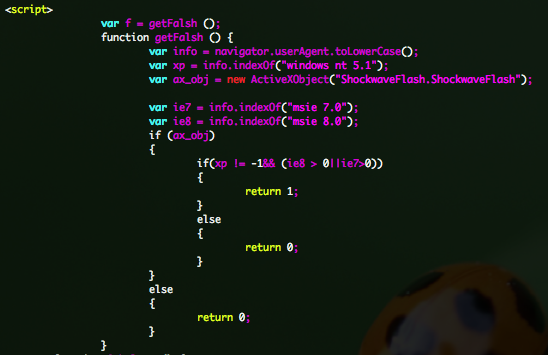
111.exe
This file is recognized as a Autodesk FLIC image file, and catched by 0 anti-viruses on VirusTotal (a5a04f661781d48df3cbe81f56ea1daae6ba3301c914723b0bb6369a5d2505d9).
Submitted to Malware Tracker (baabd0b871095138269cf2c53b517927), this file look like suspicious and require further investigations. “111.exe” is packed and after decoding the file is still not detected by any anti-virus on VirusTotal (a6086c16136ea752fc49bc987b8cc9e494384f372ddfdca85c2a5b7d43daa812). But with a Malwr analysis, you can see that this file is recognized as installing a program to run automatically at logon.
Conclusion
The guys how developed this new 0day were not happy to have been catched, they just removed all the files from the source server 2 days after my discovery. But also more interesting the also removed a Java 0day variant from other folders.
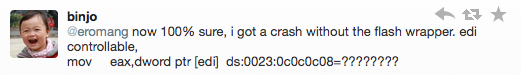
Also I submitted all these stuff to different person in order to confirm the strangeness of this exploit, and we got some good return.
Confirmed @eromang and @binjo are right about the bug.Not Adobe, appears to be IE:goo.gl/LRTXn
— sinn3r (@_sinn3r) Septembre 16, 2012
Updates:
Metasploit team is planning to release an exploit module on Monday. This module seem to work very well.
As @edistrosar predicted, yes, @_juan_vazquez_ and I r working on it, and looks good so far:goo.gl/ALR8L /cc @eromang & @binjo
— sinn3r (@_sinn3r) Septembre 16, 2012
from:http://eromang.zataz.com/2012/09/16/zero-day-season-is-really-not-over-yet/