A Brief Overview on Satellite Hacking, By Anchises Moraes Guimarães de Paula, iDefense. Information Security, July 2010 I HItb MagazIne 17.
As a large portion of worldwide Internet users increasingly rely on satellite communication technologies to connect to the Web, a number of vulnerabilities within these connections actively expose satellites to potential attacks. The implications of such a successful attack are massive, as satellites are the only means of broadcasting communications in many regions around the globe and an attacker could act from everywhere.
Satellite Hacking.pdf,下载地址:http://115.com/file/e6etli97
以下为 PDF 直接转换为纯文本,缺少大量图片,并存在大量乱码,段落严重错位,仅做参考!
------------------------------------------ ↓ PDF To TXT ↓ ------------------------------------------
----------------------- Page 1-----------------------
information security
A Brief Overview on
satellite
hacking
By Anchises Moraes Guimaraes de Paula, iDefense
JULy 2010 I HItb MagazIne 17
----------------------- Page 2-----------------------
INFORMATION SECURITy INFORMATION SECURITy
As a large portion of worldwide Internet users increasingly and telephone transmissions by using Exhibit 1. Unidirectional Access with Terrestrial Return (also known as Satmodem)8
the transponder, a radio that receives
rely on satellite communication technologies to connect a conversation at one frequency and
then amplifies it and retransmits the
to the Web, a number of vulnerabilities within these signal back to Earth on another fre-
quency that a ground-based antenna
connections actively expose satellites to potential may receive. A satellite normally con-
tains 24 to 32 transponders, which are
attacks. The implications of such a successful attack are operating on different frequencies.4
massive, as satellites are the only means of broadcasting Modern communications satellites use
a variety of orbits including geosta-
communications in many regions around the globe and an tionary orbits,5 Molniya orbits,6 other
elliptical orbits and low Earth orbits
attacker could act from everywhere. (LEO).7 Communications satellites
are usually geosynchronous because
ground-based antennas, which op-
erators must direct toward a satellite,
can work effectively without the need
roadband Internet access via satel- services, such as Global Positioning Systems to track the satellite?ˉs motion. This al-
lite is available almost worldwide. (GPSs), weather forecasts, TV transmissions lows technicians to aim satellite antennas at Internet, with outbound data traveling through
Satellite Internet services are the and mapping service applications based on an orbiting satellite and leave them in a fixed a telephone modem or a DSL connection, but it
Bonly possible method of connect- real satellite images (such as Google Maps). position. Each satellite occupies a particular sends downloads via a satellite link at a speed
ing remote areas, the sea or countries where ?°Although anything that is in orbit around location in orbit and operates at a particular near that of broadband Internet access. Two-
traditional Internet cable connections are still Earth is technically a satellite, the term ?°satel- frequency assigned by the country?ˉs regula- way satellite Internet service, also known as
not accessible. Satellite communications are lite?± typically describes a useful object placed tor as the Federal Communications Commis- bidirectional access or ?°astro-modem,?± involves
also widely adopted as backup connection in orbit purposely to perform some specific sion (FCC) in the U.S. The electromagnetic both sending and receiving data via satellite to
providers by several organizations and coun- mission or task.?±2 There are several satellite spectrum usage is regulated in every coun- a hub facility, which has a direct connection to
tries for those times when the terrestrial com- types, defined by their orbits and functions: try, so that each government has its regula- the Internet (see Exhibit 2).
munications infrastructure is not available, scientific, Earth and space observation, re- tory agency which determines the purpose
damaged or overloaded. By the end of 2008, connaissance satellites (Earth observation or of each portion of radio frequency, according The required equipment to access satellite
an estimated 842,000 US consumers relied on communications satellites deployed for mili- to international agreements. communication includes a satellite dish, a
satellite broadband Internet access.1 tary or intelligence applications) and com- receiver for satellites signals, which is a low-
munications, which include TV, voice and The satellite provider supports Internet ac- noise block (LNB) converter, a decoder, a
Communications satellites routinely receive data connections. Most satellites are custom cess and Internet applications through the satellite modem and special personal-com-
and rebroadcast data, television, image and built to perform their intended functions. provider teleport location, which connects puter software. Usually, a single device or
some telephone transmissions without the to the public switched telephone network PCI card integrates the decoder and modem.
proper security measures, leading to frequent Organizations and consumers have used sat- (PSTN) and the Internet. There are three types Several software programs and online tools
fraud and attacks against satellite ser- ellite communication technology as a means of Internet via satellite access: one-way mul- are widely available.
vices. Traditional fraud techniques to connect to the Internet via broadband ticast, unidirectional with terrestrial return
and attack vectors include satel- data connections for a long time. Internet via and bidirectional access. One-way multicast Satellite Internet customers range from indi-
lite TV hacking and the use of satellite provides consumers with connec- transmits IP multicast-based data, both audio vidual home users to large business sites with
Satellites are an
illicit decoding technology tion speeds comparable or superior to digi- and video; however, most Internet protocols several hundred users. The advantages of
to hack into television sat- tal subscriber line (DSL) and cable modems. will not work correctly because they require this technology include a greater bandwidth essential part of
ellite signals. In addition, Data communication uses a similar design a return channel. A single channel for data than other broadband technologies, nearly our daily lives.
satellite communications and protocol to satellite television, known download via a satellite link characterizes worldwide coverage, and additional sup-
are easily susceptible as Digital Video Broadcasting (DVB), a suite unidirectional access with terrestrial return, port to television and radio services. Satellite Many global
to eavesdropping if not of open standards for digital television. DVB also known as ?°satmodem?± or a ?°one-way ter- broadband service is available in areas that interactions
properly encrypted. standards are maintained by the DVB Project, restrial return?± satellite Internet system, and terrestrially based wired technologies (e.g., rely on satellite
an international industry consortium. Ser- this type of satellite access uses a data uplink cable and DSL) or wireless technologies can-
SATELLITE BASICS vices using DVB standards are available on channel with slower speed connection tech- not operate. The disadvantages, however, are communications
Satellites are an essential part every continent with more than 500 million nologies (see Exhibit 1). numerous: weather conditions (rain, storms or satellite-
of our daily lives. Many global DVB receivers deployed, including at least or solar influences) might affect satellite com- powered
interactions rely on satellite com- 3 Communica-
100 million satellite receivers. Unidirectional access systems use traditional munications, satellites demand expensive
services.
munications or satellite-powered tions satellites relay data, television, images dial-up or broadband technology to access the hardware and have a complex setup (install-
18 HItb Magaz Ine I JULy 2010 JULy 2010 I HItb MagazIne 19
----------------------- Page 3-----------------------
INFORMATION SECURITy INFORMATION SECURITy
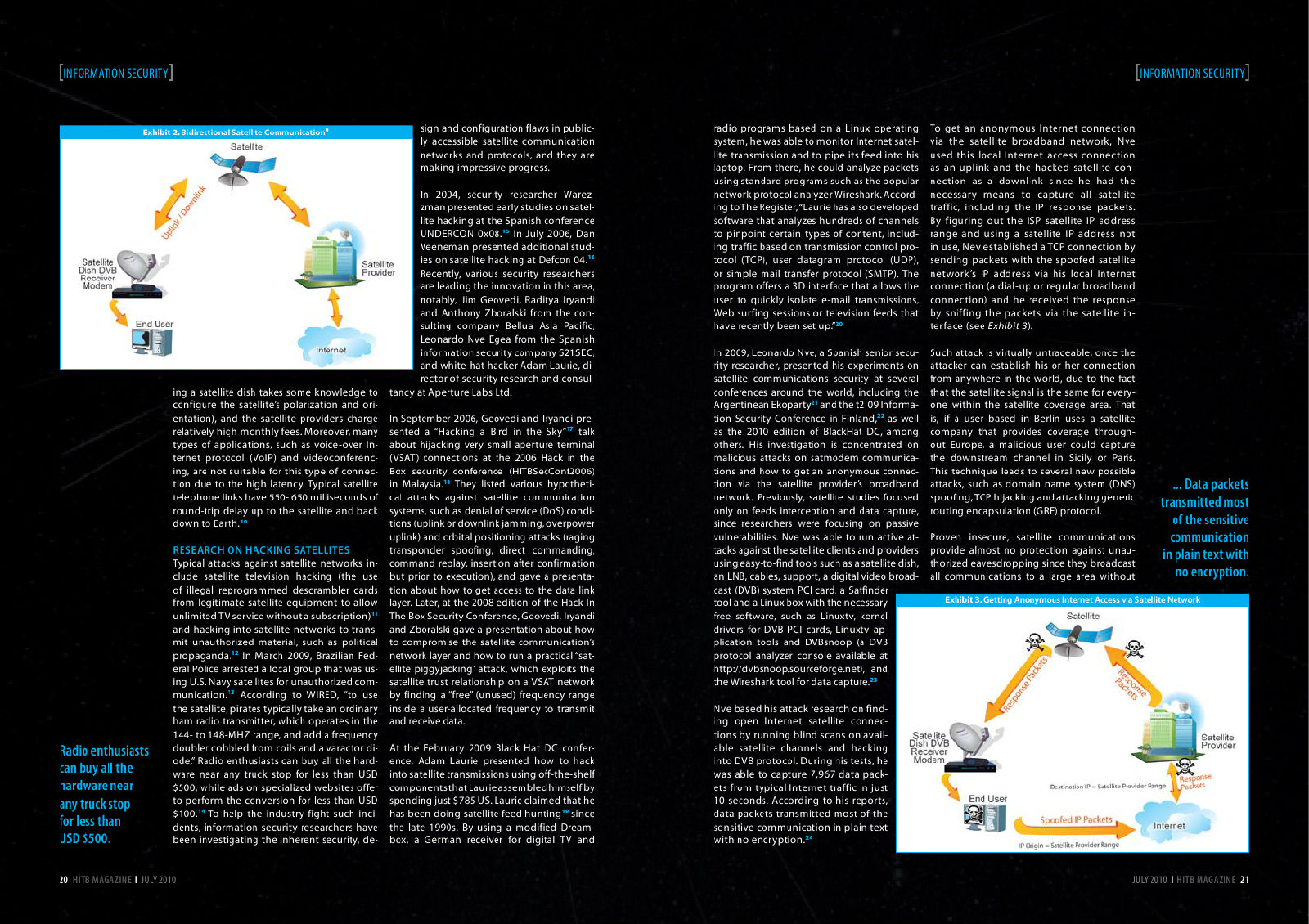
Exhibit 2. Bidirectional Satellite Communication9 sign and configuration flaws in public- radio programs based on a Linux operating To get an anonymous Internet connection
ly accessible satellite communication system, he was able to monitor Internet satel- via the satellite broadband network, Nve
networks and protocols, and they are lite transmission and to pipe its feed into his used this local Internet access connection
making impressive progress. laptop. From there, he could analyze packets as an uplink and the hacked satellite con-
using standard programs such as the popular nection as a downlink since he had the
In 2004, security researcher Warez- network protocol analyzer Wireshark. Accord- necessary means to capture all satellite
zman presented early studies on satel- ing to The Register, ?°Laurie has also developed traffic, including the IP response packets.
lite hacking at the Spanish conference software that analyzes hundreds of channels By figuring out the ISP satellite IP address
UNDERCON 0x08.15 In July 2006, Dan to pinpoint certain types of content, includ- range and using a satellite IP address not
Veeneman presented additional stud- ing traffic based on transmission control pro- in use, Nev established a TCP connection by
ies on satellite hacking at Defcon 04.16 tocol (TCP), user datagram protocol (UDP), sending packets with the spoofed satellite
Recently, various security researchers or simple mail transfer protocol (SMTP). The network?ˉs IP address via his local Internet
are leading the innovation in this area, program offers a 3D interface that allows the connection (a dial-up or regular broadband
notably, Jim Geovedi, Raditya Iryandi user to quickly isolate e-mail transmissions, connection) and he received the response
and Anthony Zboralski from the con- Web surfing sessions or television feeds that by sniffing the packets via the satellite in-
sulting company Bellua Asia Pacific; have recently been set up.?±20 terface (see Exhibit 3).
Leonardo Nve Egea from the Spanish
information security company S21SEC; In 2009, Leonardo Nve, a Spanish senior secu- Such attack is virtually untraceable, once the
and white-hat hacker Adam Laurie, di- rity researcher, presented his experiments on attacker can establish his or her connection
rector of security research and consul- satellite communications security at several from anywhere in the world, due to the fact
ing a satellite dish takes some knowledge to tancy at Aperture Labs Ltd. conferences around the world, including the that the satellite signal is the same for every-
configure the satellite?ˉs polarization and ori- Argentinean Ekoparty21 and the t2??09 Informa- one within the satellite coverage area. That
entation), and the satellite providers charge In September 2006, Geovedi and Iryandi pre- tion Security Conference in Finland,22 as well is, if a user based in Berlin uses a satellite
relatively high monthly fees. Moreover, many sented a ?°Hacking a Bird in the Sky?±17 talk as the 2010 edition of BlackHat DC, among company that provides coverage through-
types of applications, such as voice-over In- about hijacking very small aperture terminal others. His investigation is concentrated on out Europe, a malicious user could capture
ternet protocol (VoIP) and videoconferenc- (VSAT) connections at the 2006 Hack in the malicious attacks on satmodem communica- the downstream channel in Sicily or Paris.
ing, are not suitable for this type of connec- Box security conference (HITBSecConf2006) tions and how to get an anonymous connec- This technique leads to several new possible
tion due to the high latency. Typical satellite in Malaysia.18 They listed various hypotheti- tion via the satellite provider?ˉs broadband attacks, such as domain name system (DNS) ... data packets
telephone links have 550- 650 milliseconds of cal attacks against satellite communication network. Previously, satellite studies focused spoofing, TCP hijacking and attacking generic transmitted most
round-trip delay up to the satellite and back systems, such as denial of service (DoS) condi- only on feeds interception and data capture, routing encapsulation (GRE) protocol.
down to Earth.10 tions (uplink or downlink jamming, overpower since researchers were focusing on passive of the sensitive
uplink) and orbital positioning attacks (raging vulnerabilities. Nve was able to run active at- Proven insecure, satellite communications communication
RESEARCH ON HACKING SATELLITES transponder spoofing, direct commanding, tacks against the satellite clients and providers provide almost no protection against unau- in plain text with
Typical attacks against satellite networks in- command replay, insertion after confirmation using easy-to-find tools such as a satellite dish, thorized eavesdropping since they broadcast
clude satellite television hacking (the use but prior to execution), and gave a presenta- an LNB, cables, support, a digital video broad- all communications to a large area without no encryption.
of illegal reprogrammed descrambler cards tion about how to get access to the data link cast (DVB) system PCI card, a Satfinder
from legitimate satellite equipment to allow layer. Later, at the 2008 edition of the Hack In tool and a Linux box with the necessary Exhibit 3. Getting Anonymous Internet Access via Satellite Network
unlimited TV service without a subscription)11 The Box Security Conference, Geovedi, Iryandi free software, such as Linuxtv, kernel
and hacking into satellite networks to trans- and Zboralski gave a presentation about how drivers for DVB PCI cards, Linuxtv ap-
mit unauthorized material, such as political to compromise the satellite communication?ˉs plication tools and DVBsnoop (a DVB
propaganda.12 In March 2009, Brazilian Fed- network layer and how to run a practical ?°sat- protocol analyzer console available at
eral Police arrested a local group that was us- ellite piggyjacking?± attack, which exploits the http://dvbsnoop.sourceforge.net), and
ing U.S. Navy satellites for unauthorized com- satellite trust relationship on a VSAT network the Wireshark tool for data capture.23
munication.13 According to WIRED, ?°to use by finding a ?°free?± (unused) frequency range
the satellite, pirates typically take an ordinary inside a user-allocated frequency to transmit Nve based his attack research on find-
ham radio transmitter, which operates in the and receive data. ing open Internet satellite connec-
144- to 148-MHZ range, and add a frequency tions by running blind scans on avail-
radio enthusiasts doubler cobbled from coils and a varactor di- At the February 2009 Black Hat DC confer- able satellite channels and hacking
ode.?± Radio enthusiasts can buy all the hard- ence, Adam Laurie presented how to hack into DVB protocol. During his tests, he
can buy all the ware near any truck stop for less than USD into satellite transmissions using off-the-shelf was able to capture 7,967 data pack-
hardware near $500, while ads on specialized websites offer components that Laurie assembled himself by ets from typical Internet traffic in just
any truck stop to perform the conversion for less than USD spending just $785 US. Laurie claimed that he 10 seconds. According to his reports,
$100.14 To help the industry fight such inci- has been doing satellite feed hunting19 since data packets transmitted most of the
for less than
dents, information security researchers have the late 1990s. By using a modified Dream- sensitive communication in plain text
USd $500. been investigating the inherent security, de- box, a German receiver for digital TV and with no encryption.24
20 HItb Magaz Ine I JULy 2010 JULy 2010 I HItb MagazIne 21
----------------------- Page 4-----------------------
Advertisement
High Security Lab: http://lhs.loria.fr
INFORMATION SECURITy
proper confidentiality controls. Various pas- >>references Malware 2010
sive and active threats against insecure In-
ternet satellite communications include sniff- 1.?°State of the Satellite Industry Report.?± June 2009. Satellite Industry Association.
ing, DoS attacks and establishing anonymous http://www.sia.org/news_events/2009_State_of_Satellite_Industry_Report.pdf.
connections. Hacking into satellite receivers 2. Brown, Gary. ?°How Satellites Work.?± HowStuffWorks. http://science.howstuffworks.
com/satellite1.htm. Accessed on Nov. 5, 2009.
is much easier now than it was in the past, 3. ?°Introduction to the DVB Project.?± Mar. 23, 2010. DVB. http://www.dvb.org/
thanks to the widespread availability of Linux technology/fact_sheets/DVB-Project_Factsheet.pdf.
tools and several online tutorials. 4. ?°Satellite Technology.?± Nov. 5, 2009. Satellite Broadcasting & Communications
Association (SBCA). http://www.sbca.com/receiver-network/satellite-receiver.htm.
5. Geostationary orbits (also called geosynchronous or synchronous orbits) are
CONCLUSION
orbits in which a satellite always positions itself over the same spot on Earth.
Governmental, Military organizations and Many geostationary satellites (also known as Geostationary Earth Orbits, or GEOs)
most of the companies included within the orbit above a band along the equator, with an altitude of about 22,223 miles.
critical infrastructure sector such as transport, (Brown, Gary. ?°How Satellites Work.?± HowStuffWorks. http://science.howstuffworks.
com/satellite5.htm. Accessed on Nov. 5, 2009.)
oil and energy, are using satellite communi- 6.The Molniya orbit is highly eccentric ?a the satellite moves in an extreme ellipse with
cations for transmitting sensitive information the Earth close to one edge. Because the planet?ˉs gravity accelerates it, the satellite
across their widespread operations. This in- moves very quickly when it is close to the Earth. As it moves away, its speed slows,
cludes the use of satellite communication at so it spends more time at the top of its orbit farthest from the Earth. (Holli Riebeek.
?°Catalog of Earth Satellite Orbits / Three Classes of Orbit.?± Nov. 5, 2009. NASA Earth
industrial plants operating supervisory control Observatory. http://earthobservatory.nasa.gov/Features/OrbitsCatalog/page2.php.)
and data acquisition (SCADA) systems. The rel- 7. A satellite in low Earth orbit (LEO) circles the earth 100 to 300 miles above the
evance of satellite communication protection Earth?ˉs surface..(?°What Is a Satellite??± Satellite Industry Association. Nov. 5,
and the consequences of a security incident 2009. Boeing. http://www.sia.org/industry_
overview/sat101.pdf.)
should enforce these organizations to deploy 8. Warezzman. ?°DVB: Satellite Hacking For
additional security measures to their internal Dummies.?± 2004. Undercon. http://www.
communication technologies. Companies and undercon.org/archivo/0x08/UC0x08-DVB-
organizations that use or provide satellite data Satellite_Hacking.pdf.
9. Based on ?°DVB: Satellite Hacking for
connections must be aware of how insecure
Dummies?± by Warezzman source: http://
satellite connections are and aware of the pos- www.undercon.org/archivo/0x08/UC0x08-DVB-Satellite_
sible threats in this environment. Companies Hacking.pdf.
and users must implement secure protocols to 10. Brown, Gary. ?°How Satellites Work.?± HowStuffWorks.
http://science.howstuffworks.com/satellite7.htm. 5th IEEE International Conference
provide data protection, such as virtual private Nov. 5, 2009.
network (VPN) and secure sockets layer (SSL), 11. Berry, Walter. ?°Arrests Made in TV Satellite on Malicious and U wanted Software
since most traffic transmits unencrypted and Hacking.?± Jan. 25, 2009. abc News. http://abcnews.
is widely available in a large geographic area go.com/Technology/story?id=99047. Nancy, France, Oct. 20-21, 2010
12. Morrill, Dan. ?°Hack a Satellite while it is in orbit.?± April 13, 2007. Toolbox for IT. http://
under the satellite?ˉs coverage. it.toolbox.com/blogs/managing-infosec/hack-a-satellite-while-it-is-in-orbit-15690. http://malware10.loria.fr
13.?°PF descobre equipamento capaz de fazer ??gato?ˉ em sat¨|lite dos EUA?± (?°PF discovered
ABOUT THE AUTHOR equipment to hook into U.S. satellite?±). March 19, 2009. Jornal da Globo. (Global
Anchises M. G. de Paula, CISSP, is an Interna- Journal). http://g1.globo.com/Noticias/Tecnologia/0,,MUL1049142-6174,00-PF+DESCO Important dates Program Committee
BRE+EQUIPAMENTO+CAPAZ+DE+FAZER+GATO+EM+SATELITE+DOS+EUA.html.
tional Cyber Intelligence Analyst at iDefense, 14. Soares, Marcelo. ?°The Great Brazilian Sat-Hack Crackdown.?± Apr. 20, 2009. WIRED. Submission: June 30th, 2010 Anthony Arrott, Trend Micro
a VeriSign company. He has more than 15 http://www.wired.com/politics/security/news/2009/04/fleetcom. Notification: August 27th, 2010 Pierre-Marc Bureau, ESET
years of strong experience in Computer Secu- 15. Undercon home page. http://www.undercon.org/archivo.php?ucon=8. Accessed
on Nov. 5, 2009. Final version: September 10th, 2010 Mila Dalla Preda, Verona University
rity, and previously worked as Security Officer
in Brazilian telecom companies before be- 16. DEF CON IV home page. http://www.defcon.org/html/defcon-4/defcon-4.html. Saumya Debray, Arizona University
Accessed on Nov. 5, 2009.
coming Security Consultant for local infosec 17. Note: ?°Bird?± is a term for satellite. General Program Chair Thomas Engel, University of Luxembourg
resellers and consulting companies. Anchises 18. HITBSecConf2006 home page. http://conference.hitb.org/hitbsecconf2006kl. Jos¨| M. Fernandez, Ecole Polytechnique de
Accessed on Nov. 5, 2009. Fernando C. Colon Osorio, WSSRL and
holds a Computer Science Bachelor degree Montr¨|al
from Universidade de Sao Paulo (USP) and a 19. Note: ?°Feed Hunting?± means looking for satellite feeds that no one is supposed to find. Brandeis University
20. Goodin, Dan. ?°Satellite-hacking boffin sees the unseeable.?± Feb. 17, 2009. The Dr. Olivier Festor, INRIA
master degree in Marketing from ESPM. He Register. http://www.theregister.co.uk/2009/02/17/satellite_tv_hacking. Chairs of Malware 2010
has also obtained various professional cer- 21. Ekoparty Security Conference home page. http://www.ekoparty.com.ar. Jean-Yves Marion, Nancy University Prof. Brent Kang, North Carolina University
tificates including CISSP, GIAC (Cutting Edge Accessed on Nov. 5, 2009. Noam Rathaus, Beyond Security Prof. Felix Leder, Bonn University
Hacking Techniques) and ITIL Foundations. 22. t2??09 Information Security Conference home page. http://www.t2.fi/conference. Bo Olsen, Kaspersky
Accessed on Nov. 5, 2009. Cliff Zhou, University Central Florida
As an active member of Brazilian infosec com- 23. Nve, Leonardo. ?°Playing in a Satellite environment 1.2.?±). Black Hat. http:// Dr. Jose Nazario, Arbor networks
munity, he was the President of ISSA Chapter blackhat.com/presentations/bh-dc-10/Nve_Leonardo/BlackHat-DC-2010-Nve- Publicity Co-Chairs Dr. Phil Porras, SRI International
Brazil in 2009 and one of the founding mem- Playing-with-SAT-1.2-wp.pdf. Accessed on May 28, 2010. Jose Morales, University of Texas Fred Raynal, Sogeti
bers of Brazilian Hackerspace and Brazilian 24. Nve, Leonardo. ?°Sat¨|lite: La senal del cielo que estabas esperando (II)?± (?°Satellite: Daniel Reynaud, Nancy-University
The sign from sky that you were waiting for (II)?±). Jan. 16, 2009. S21sec. http:// Andrew Walenstein, Lafayette University
Cloud Security Alliance chapter. * blog.s21sec.com/2009/01/satlite-la-seal-del-cielo-que-estabas_16.html. Local Chair
Jeff Williams, Microsoft
Matthieu Kaczmarek, INRIA
Yang Xiang, Deakin University
22 HItb MagazIne I JULy 2010